write a program to output the factorial of a number given a a integer n (user input), where n is from 1 up to 10 only using switch case statement. note: factorial can get very big given a big n, you need to be careful with simple implementation in loop, but we are just practice switch case in this question.[
Answers
The prompt is asking for a program to calculate the factorial of a user-input number between 1 and 10, using a switch case statement instead of a loop implementation.
What is the prompt asking for?The prompt is asking for a program that calculates the factorial of a number input by the user, with the restriction that the input must be between 1 and 10.
The program should use a switch case statement to handle the different cases of the input, rather than a traditional loop implementation.
It is important to note that factorials can get very large quickly, so the program should be careful not to cause overflow errors.
However, since this prompt is specifically focused on practicing switch case statements, the program should prioritize meeting that requirement while also calculating the factorial of the given input.
Learn more about program
brainly.com/question/30613605
#SPJ11
Related Questions
give me rationale about brake system???
Answers
The brake system in a vehicle plays a critical role in ensuring safety, control, and efficient operation.
Here are some rationales for the importance of a well-designed and functioning brake system:
1)Safety: The primary purpose of the brake system is to provide reliable and efficient stopping power, allowing the driver to slow down or bring the vehicle to a complete stop when necessary.
A properly functioning brake system is crucial for avoiding accidents, preventing collisions, and protecting the driver, passengers, and others on the road.
2)Control and Handling: A well-designed brake system enhances the driver's control over the vehicle.
It enables smooth deceleration and allows for precise modulation of braking force, providing better handling and maneuverability.
This allows the driver to respond to changing road conditions, traffic situations, and emergencies effectively.
3)Energy Conversion: The brake system converts kinetic energy into thermal energy through friction, allowing the vehicle to reduce its speed or stop.
This energy conversion process is essential for managing the vehicle's speed and preventing excessive heat buildup in the braking components.
4)Performance and Responsiveness: An efficient brake system ensures prompt response and reliable performance, allowing the driver to trust the brakes when needed.
It should provide consistent braking force, even under different driving conditions such as wet or slippery surfaces.
A well-designed brake system improves the overall driving experience by instilling confidence and predictability in the braking process.
5)Maintenance and Longevity: Regular maintenance of the brake system, including inspections, pad and rotor replacements, and fluid flushes, is crucial for its longevity and optimal performance.
A properly maintained brake system minimizes the risk of component failure, extends the lifespan of brake components, and reduces the chances of costly repairs.
For more questions on brake system
https://brainly.com/question/30262553
#SPJ8
Katrina wants to get a random number and assign it to a variable called force. Which line of code should be used?
orce = random.randint(1,10)
force = random(1,10)
force = randint(1,10)
force == random.randint(1,10)
Answers
Since Katrina wants to get a random number and assign it to a variable called force the code to be used is
force = random.randint(1, 10)
How will the above code work?This line uses the randint function from the random module to generate a random integer between 1 and 10 (inclusive) and assigns it to the variable force
Computer code is a set of instructions or a set of rules written in a specific programming language (i.e., the source code) in computer programming.
Learn more about code at:
https://brainly.com/question/26134656
#SPJ1
an example of intangible property is
Answers
Answer:
Examples of intangible property include
patents, patent applications, trade names, trademarks, service marks, copyrights, trade secrets. Some intangible property might have a paper embodiment, (such as stocks, bonds, or certificates) but other intangible property does not (intellectual property).
Explanation:
I hope it helps
There are things that can't be touched yet nevertheless have worth, known as intangible property. The example of intangible property is a song.
What is an intangible Property?Intangible property, usually referred to as inanimate property, is anything that a person or business can possess and hand over control to another individual or company but has no physical counterpart, such as a company's name or understanding property.
It typically relates to legal creations like patents, trademarks, and copyright. It does not include material possessions like real estate (soil, buildings, and furnishings) and personal property.
Intangible assets are also known as options in action in some legal systems. A distinction is made between tangible and intangible property. There are two types of intangible property: competitive intangible property and legal intangible items, which are both described here.
To know more about Intangible Property:
https://brainly.com/question/29511956
#SPJ12
Please complete the following program according to the specification given. Partial credit will be given for incomplete answers, so provide as much of the answer as you can. Remember that all program segments are to be written in JAVA.
1.Write a method split() which takes an argument String s and prints each character of s with a comma(“,”) in between each character.
Example
split(“1234”) prints: “1,2,3,4”
split(“Hi, Mr. Programmer!”) prints “H,i,,, , M,r,., P,r,o,g,r,a,m,m,e,r,!”
split(“”) prints “”
static public void split(String s) {
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that write a method split() which takes an argument String s and prints each character of s with a comma(“,”) in between each character.
Writting the code:import java.io.*;
public class Test
{
public static void main(String args[])
{
String Str = new String("Geeks-for-Geeks");
// Split above string in at-most two strings
for (String val: Str.split("-", 2))
System.out.println(val);
System.out.println("");
// Splits Str into all possible tokens
for (String val: Str.split("-"))
System.out.println(val);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

16. What's the difference between a footnote and endnote?
A. Footnotes are typically at the bottom of the page, while endnotes are at the bottom of the
document.
B. Footnotes are typically within the document, while endnotes are at the bottom of the
page.
O C. There's no difference; footnotes and endnotes are the same thing.
O D. Endnotes are typically at the bottom of the page, while footnotes are at the end of the
document.
Answers
Answer:
I believe it is 'A'
Explanation:
Footnotes appear at the bottom of the relevant page. Endnotes appear in a list at the end of the text, just before the bibliography.
The one difference between footnotes and endnotes is that footnotes appear at the bottom of the same page, while endnotes appear at the end of the paper.
What is footnote?A footnotes is known to be a short sentence or words that are often written in the bottom of a given or same page.
Note that the endnotes only shows at the end of the paper and as such The one difference between footnotes and endnotes is that footnotes appear at the bottom of the same page, while endnotes appear at the end of the paper.
Learn more about footnote from
https://brainly.com/question/1481437
#SPJ2
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
cisco's configuration rollback, vmware snapshot, windows steady state, linux systemback, and mac's time machine all offer what capability?
Answers
Built-in backup software for Macs called Time Machine was unveiled with Mac OS X Leopard. It's a fantastic program that will frequently backup your files.
Additionally, it allows you to view individual previously backed-up files or folders, which is a useful tool if you want to preview a file before recovering it. Your Mac's built-in Time Machine backup feature may be used to regularly back up all of your personal information, including programs, music, photographs, emails, and documents. You can restore deleted or inaccessible files if you have a backup. To move your files, choose one of the following actions after clicking the Finder icon in the Dock to launch a Finder window. Transfer documents to the storage device.
Learn more about storage here-
https://brainly.com/question/13041403
#SPJ4
sally just finished the third iteration in her architectural analytics platform. the team has a large product backlog that is supported by several user stories. sally is in the process of planning the next sprint and recent finished prioritizing the product backlog. she has identified several user stories for the next iteration and has already assigned them weighted values. she has been asked by the board of directors to provide an estimated time to completion for the next iteration. what technique would be best?
Answers
Sally's team's creation of a draft PI plan for the PI's iterations, authoring of draft PI Objectives, and identification of program risks and concerns are all facilitated by the SAFe Scrum Master.
What is iteration planning?During an iteration planning meeting, the team members decide how much of the team backlog they can commit to completing in the coming iteration. With the help of determined Iteration Goals, the team distills their effort.
Additionally, they assist the team in setting up their actual or virtual planning areas by supplying visual radiators that promote cooperation and communication. The iteration backlog is updated daily by team members who put features into practice and test them. A feature is taken off the backlog once it has received the thumbs-up from a customer or product manager and fulfills the done standards.
To learn more about iteration planning, visit:
https://brainly.com/question/15123677
#SPJ4
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
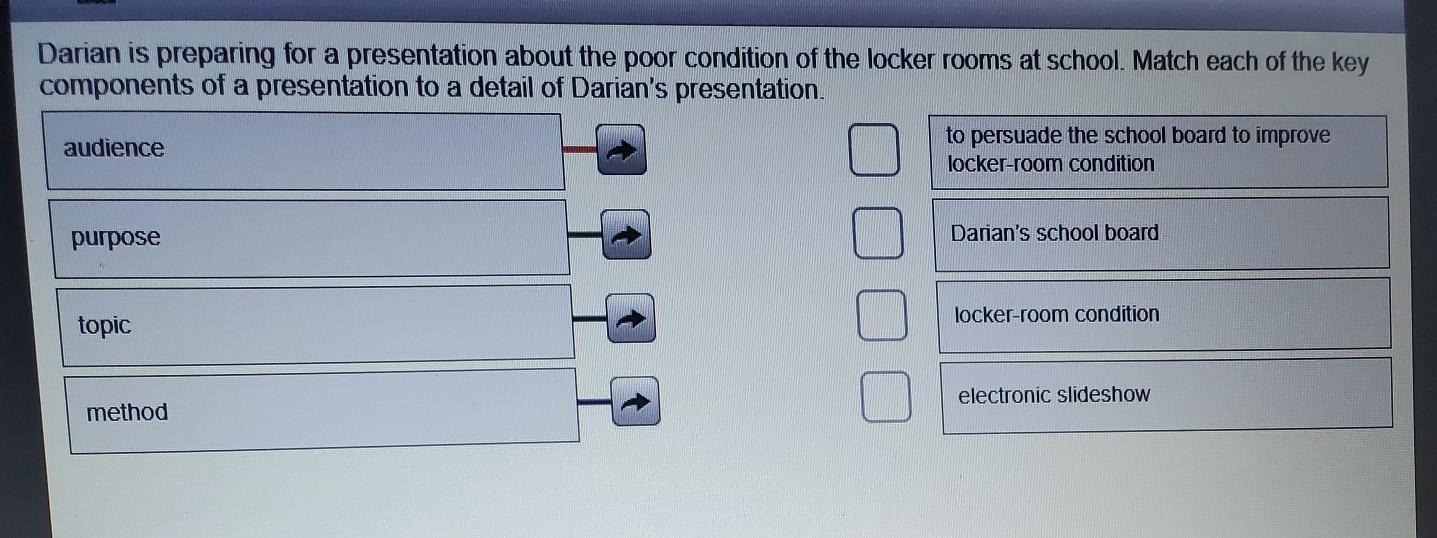
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
Name at least 5 components/features that should be on any map and give a brief description of the importance of each.
Answers
Five essential components/features: title, legend/key, scale, compass rose, and labels. Each component serves a specific purpose in providing important information and enhancing the usability of the map.
1. Title: The title of a map provides a brief description or name of the area represented, allowing users to quickly identify the subject of the map. It helps establish context and aids in understanding the purpose of the map.
2. Legend/Key: The legend or key is a critical component that explains the symbols, colors, and patterns used on the map. It provides a guide to interpret the map's features, such as landmarks, roads, bodies of water, or thematic information. The legend enhances the map's clarity and ensures proper understanding.
3. Scale: The scale on a map represents the relationship between the measurements on the map and the corresponding distance on the ground. It helps users understand the actual size or distance of features on the map. A scale is crucial for accurate measurement, navigation, and estimating travel times or distances.
4. Compass Rose: The compass rose is a graphical representation of the cardinal directions (north, south, east, west) and intermediate directions (northeast, southeast, southwest, northwest). It provides orientation and helps users understand the directionality of the map.
5. Labels: Labels are text-based identifiers placed on the map to indicate the names of places, landmarks, geographical features, or other relevant information. Labels help users navigate and locate specific areas or objects on the map, improving the map's usability and understanding.
By including these essential components/features on a map, users can quickly grasp the subject, interpret symbols and colors, understand distances and directions, and locate specific places or features. These elements contribute to effective communication and usability, making the map informative and user-friendly.
To learn more about labels visit:
brainly.com/question/32060242
#SPJ11
Why do you think that so many of these sources have similar names?
Answers
Find out how to print the below pattern in python and also come up with pseudocode,
you have to use for loop for this, you can use a for loop inside the outer for loop.
You can't use operator like " *" in python , only use print statement to print the below pattern. Find out how to print in 5 lines one by one in python , there is a way to print one line then next
X
XXX
XXXXX
XXXXXXX
XXXXXXXXX
Answers
Answer:
for i in range(5):
for j in range(2*i + 1):
print("*", end="")
print()
Explanation:
for row index going from 0 to 5
for column index going from 0 to 2*row index + 1
print * suppressing new line
print a new line to move to next row
Why do people enjoy codehs
Answers
Answer: this is a moral question, but here is my view
Explanation:
we get to learn about things like java which i am currently learning for AP computer science A
What is the sum of
1
7
10
and
3
3
5
? Use the fraction strips to help.
An image shows two groups of fraction strips. The first group is one one-whole fraction strip and seven one-tenth fraction strips. Under the first group, the second group is three whole fraction strips and six one-tenth fraction strips.
A.
4
7
10
B.
5
C.
5
3
10
D.
3
1
2
Answers
Answer
\(1\frac{7}{10} + 3\frac{3}{5} = 5\frac{3}{10}\)
Explanation:
Given
\(1\frac{7}{10} + 3\frac{3}{5}\)
Required: Evaluate the sum
\(1\frac{7}{10} + 3\frac{3}{5} =\)
Convert to improper fraction
\(1\frac{7}{10} + 3\frac{3}{5} = \frac{17}{10} + \frac{18}{5}\)
Take LCM
\(1\frac{7}{10} + 3\frac{3}{5} = \frac{17+36}{10}\)
\(1\frac{7}{10} + 3\frac{3}{5} = \frac{53}{10}\)
Convert to mixed fraction
\(1\frac{7}{10} + 3\frac{3}{5} = 5\frac{3}{10}\)
Answer:
c
Explanation:
What is the best way to protect computer equipment from damage caused by electrical spikes?
Connect equipment using a USB port.
Turn off equipment that’s not in use
Recharge equipment batteries regularly.
Plug equipment into a surge protector.
Answers
Answer:
Plug equipment into a surge protector
Explanation:
Surge protectors will take most electrical spikes.
Connecting equipment via USB port is ok if it's connected to a surge protector.
Turning off equipment when it is not in use helps the battery, but the battery can still be messed up even when it's off because of electrical spikes.
Recharging equipment batteries is good when you don't have power for it, and when you need to use it.
Connecting computer equipment via a USB port is the best way to protect it from damage caused by electrical spikes.
What exactly is an electrical spike?Spikes are fast, short-duration electrical transients in voltage (voltage spikes), current (current spikes), or transferred energy (energy spikes) in an electrical circuit in electrical engineering. A power surge can be caused by a number of factors. The most common causes are electrical overload, faulty wiring, lightning strikes, and power restoration following a power outage or blackout. Lightning, static electricity, magnetic fields, and internal changes in voltage use can all cause voltage spikes and surges. A surge protector is the best way to protect your electronic equipment.Therefore,
Connect your equipment to a surge protector, which will absorb the majority of the surge of electricity. If you connect everything via USB to a surge protector, you should be fine. Turning off the equipment when not in use will only extend the battery's life; if it is spiked while turned off, it will still be damaged. Recharging equipment is only useful when there is no power and you need to use a specific device. So, now that I've covered all of your options, it should be clear that plugging your electronics into a surge protector is the best option.
To learn mote about USB port, refer to:
https://brainly.com/question/19992011
#SPJ1
what is the easiest way not to get distracted from doing my school work?
Answers
Answer:
really you want the answer
Answer:
Find a good quiet place, Turn off your phone. put it away, wear comfy clothes, Lock your door. Dont eat, But drink water
Explanation:
Hope this helped!
A client computer networked to a server computer, with processing split between the two types of machines, is called a(n):
Answers
Answer:
two-tiered client/server architecture
Explanation:
The working area used to design and lay out content which is displayed during the presentation
Answers
Answer:
Outline tab is the answer
you are running macos mojave and you want to begin working with various other oss such as windows server and linux. you only have one computer and you need to keep using macos while working with the other oss. what can you install on macos that will help achieve this goal? a. esxi server b. vmware fusion c. vmware workstation d. hyper-v for macos
Answers
You wish to start collaborating with various other operating systems, such as linux and windows server, while using macOS Mojave. You only have one computer, thus you have to continue using Mac OS X while utilizing the other OS. VMware Fusion must be set up.
A macOS update installation issue could happen for a variety of different causes. Ideally, the error message was clear in describing the issue. You'll be able to focus your troubleshooting efforts accordingly.
You can get caught in a loop where the installer keeps opening every time you restart your computer if your macOS installation couldn't be finished. Before attempting to fix the issue, use these fast steps to get out of the loop and safeguard your data.
learn more about VMware Fusion
https://brainly.com/question/4682288
#SPJ4
Help!!! Photography class!! ASP
Which of the following represents aperture priority mode?
Select all that apply.
Α.
The photographer needs to select the value of aperture manually.
B.
The camera determines the value of aperture automatically.
С
The camera determines the value of shutter speed automatically.
D
The photographer needs to select the value of shutter speed manually.
Answers
Answer:
D.
Explanation:
Typically represented by a capital A (or sometimes Av, short for Aperture Value) on the camera mode dial, aperture priority allows the photographer to dial in this specific exposure setting—the ƒ-stop—and asks the camera to calculate the correct corresponding shutter speed in the instant before the shutter is released.
Write a program that takes a decimal number from the user and then prints the integer part and the decimal part separately. For example, if the user enters 2.718, the program prints: Integer part = 2 and decimal part = .718 in python
Answers
Answer:
Explanation:
The following was coded in Python as requested. It is a function that takes in a number as a parameter. It then uses the Python built-in math class as well as the modf() method to split the whole number and the decimal, these are saved in two variables called frac and whole. These variables are printed at the end of the program. The program has been tested and the output can be seen below.
import math
def seperateInt(number):
frac, whole = math.modf(number)
print("Whole number: " + str(math.floor(whole)))
print("Decimals number: " + str(frac))

write a bash script that computes the sum of the absolute values of integers given by standard input
Answers
Here is a bash script that calculates the sum of the absolute values of integers given by standard input:
```
#!/bin/bash
sum=0
while read -r num; do
if [[ $num -lt 0 ]]; then
num=$((num*-1))
fi
sum=$((sum+num))
done
echo "The sum of the absolute values is $sum."
```
The `sum` variable is initially set to 0. The `while` loop reads integers from standard input one by one, until there are no more left to read. Inside the loop, we check if the integer is negative using an `if` statement.
If it is, we convert it to its absolute value by multiplying it by -1. We then add the absolute value of the integer to the `sum` variable. After all the integers have been read and processed, the bash script prints out the final value of `sum`.
Learn more about bash script https://brainly.com/question/27962326
#SPJ11
Question Mode Matching Question Match the following description with the appropriate programming language generation. 1GL 1GL drop zone empty. 2GL 2GL drop zone empty. 3GL 3GL drop zone empty. 4GL 4GL drop zone empty. 5GL 5GL drop zone empty. Extremely advanced. Uses statements (scripts) rather than algorithms. High-level programming language. Uses a compiler to convert into machine language. Machine language. Represented by a series of 1s and 0s. Assembly language. An assembler converts 2GL into machine language. Specifically designed for creating database management programs.
Answers
Answer:
1GL: Machine language. Represented by a series of 1s and 0s.
2GL: Assembly language. An assembler converts 2GL into machine language.
3GL: High-level programming language. Uses a compiler to convert into machine language.
4GL: Specifically designed for creating database management programs.
5GL: Extremely advanced. Uses statements (scripts) rather than algorithms.
Explanation:
Programming languages started as a series of binary digits (i.e. 0's and 1'). This generation of language is referred to as the first generation.
However, the machine language were difficult to read by human, so mnemonics were created (i.e. assembly language). This language uses symbolic codes such as ADD for addition, etc. This is the second generation
The third generation are the high level languages that uses languages that can be easily understood by human, e.g. + means plus. However, the language must be translated; hence the need for a compiler or interpreter, as the case may be.
The fourth and fifth generations are extensions of the third generation languages. The fourth were created to connect to DBMS while the fifth are more advanced.
which flag is required to be set to "on" in an ra for a host to send a request to a dhcpv6 server?
Answers
The flag that needs to be set to "on" in an RA (Router Advertisement) for a host to send a request to a DHCPv6 server is the Managed Address Configuration (M) flag.
When this flag is set to "on", it indicates to the host that it should obtain its IPv6 address through DHCPv6 rather than generating it itself. In IPv6 networking, Router Advertisement (RA) messages are used by routers to advertise their presence and provide configuration information to hosts on the network.
One of the configuration options that can be included in an RA message is the Managed Address Configuration (M) flag. When the M flag is set to "on" in an RA message, it indicates that hosts on the network should use DHCPv6 (Dynamic Host Configuration Protocol for IPv6) to obtain IPv6 addresses.
Learn more about Managed Address Configuration: https://brainly.com/question/31055079
#SPJ11
There are many options for using Python in the cloud. What should you check if you experience errors with standard syntax? Select an answer: the compression method the version of the Python kernel being used the fonts and color schemes for the editor the version of the exercise files
Answers
If you encounter errors with standard syntax while using Python in the cloud, it is recommended to check the version of the Python kernel being used as it could be incompatible with the version of the programming language you're using.
If you experience errors with standard syntax while using Python in the cloud, you should check the version of the Python kernel being used.
Python is a popular high-level programming language for general-purpose programming. It's utilized in web development, data analysis, artificial intelligence, scientific computing, and other fields. Python is open-source software, which means it's free to use and distribute.
Cloud computing is a model for delivering services on-demand over the internet, like servers, storage, databases, networking, software, analytics, and intelligence, rather than using your local server or computer. The pay-as-you-go service is accessible from any location with an internet connection.
There are various options for using Python in the cloud. Let's have a look at some of the most common ones:
Web Services: It's a collection of remote computing services provided. It provides cloud computing services that can help you get your project up and running quickly.Azure: It's a cloud computing service created by that is frequently used for building, testing, deploying, and managing applications and services through a network of managed data centers.Cloud Platform: It's a collection of cloud computing services provided. It provides cloud computing services that can help you get your project up and running quickly.OpenShift: OpenShift is a container application platform for deploying and managing cloud-native applications that allows you to deploy and scale your Python applications in the cloud.If you experience errors with standard syntax while using Python in the cloud, you should check the version of the Python kernel being used. This may occur if the kernel version used is incompatible with the version of the programming language you're using.
Learn more about standard syntax: brainly.com/question/20935990
#SPJ11
Find the length of the shorter leg in the triangle pictured below
x=6
x=24
X=12
X=12 square root 3
X=36

Answers
Falling If the user doesn't do anything, the player sprite should fall. Do This • Find the code comment // FALLING . • Use the counter pattern with the player sprite's velocityy to make the flyer fall. Test your code to make sure that it works. The sprite should fall faster as it goes down the . screen. Toolbox ♡ Workspace World Sprites 1 77 GAME SETUP Drawing Control 2 // create player, target, and obstacles Math Variables 3 var rock = createSprite(109 100) var sprite = createSpritex, 4 rock.scale = 0.5; sprite.setAnimation (label) 5 var player createSprite(200, 100) 1: player.setAnimation "fly_bot"); sprite.x 6
Answers
__________ specifies a number of features and options to automate the negotiation, management, load balancing, and failure modes of aggregated ports.
Answers
The Link Aggregation Control Protocol (LACP) specifies a number of features and options to automate the negotiation, management, load balancing, and failure modes of aggregated ports.
Link Aggregation Control Protocol (LACP) is an IEEE 802.3ad standard protocol that provides a way to group several physical Ethernet connections into a single logical interface that is referred to as a Link Aggregation Group (LAG), virtual interface, or aggregate interface.The LACP protocol automates the process of creating, managing, and monitoring these aggregated interfaces. It can be used for both switch-to-switch and switch-to-server connections. The protocol specifies a number of features and options that allow administrators to control the way in which ports are grouped and the criteria used to distribute traffic across them.
The features and options specified by LACP include:
Automatic configuration and management of LAGs using Dynamic Link Aggregation (DLA).
Load balancing of traffic across the aggregated links using a configurable algorithm.
Fault tolerance and failover protection using a range of failure modes and load-balancing policies.
To know more about Link Aggregation Control Protocol visit:
https://brainly.com/question/32764142
#SPJ11
All internet traffic should be treated equally. This is called?
Answers
All internet traffic should be treated equally. This is called net neutrality.
Network neutrality ensures that all data on the internet is treated equally by internet service providers (ISPs) and governments, regardless of content, user, platform, application, or device. For users, net neutrality enables access and transparency of internet content and allows access to all internet services and applications.
Net neutrality fulfils an important role in ensuring that people can freely access information and impart ideas across our information society. It promotes diversity, pluralism, and innovation.
Here you can learn more about Network neutrality
brainly.com/question/13165766
#SPJ4
Match each Animation category to its description

Answers
Answer:
Your photo is 100% correct
Explanation: protect question from longwinded or poor answers complete.
Motion path: move object on screen. Emphasis: make an object stand out. Entrance: move an object top the frame. Exit: move object out of the frame.
What is animation?Animation is the process of creating the illusion of motion and change by rapidly displaying a sequence of static images that minimally differ from each other.
The terms commonly used in animation and video production:
The path that an object takes as it moves across the screen is referred to as its motion path. A straight line, a curve, or any other shape or pattern can be used.The use of animation techniques to draw attention to a specific object or element on the screen is referred to as emphasis. This can be accomplished by utilising colour, size, movement, or other visual effects.The animation of an object as it enters the screen or frame is referred to as its entrance. This can be accomplished through the use of various techniques such as a slide, a fade-in, or a zoom-in effect.Exit: the animation of an object leaving the screen or frame. This can be accomplished through the use of various techniques such as a slide, a fade-out, and so on.Thus, this can be the match for the given scenario.
For more details regarding animation, visit:
https://brainly.com/question/29996953
#SPJ3