write one line HTML code to make the 'I love India' text bold with a line drawn through the middle of it
Answers
The line of HTML code to make the 'I love India' text bold with a line drawn through the middle of it is:
<s><b>I love India</b></s>
What is HTML?HTML, or HyperText Markup Language, is the standard markup language for texts intended to be displayed in a web browser. It is frequently aided by technologies like Cascading Style Sheets and programming languages like JavaScript.
HTML, or Hypertext Markup Language, is a computer language that is used to define the structure of web pages. HTML allows you to construct static pages with text, headers, tables, lists, graphics, and links, among other things.
Learn more about HTML code at:
https://brainly.com/question/14793584
#SPJ1
Related Questions
How many NOTS points are added to your record for not completely stopping at a stop sign?
Answers
In some jurisdictions, failing to stop at a stop sign can result in a citation for running a stop sign or a similar violation. In other jurisdictions, it may be categorized as a failure to obey traffic signals or a similar violation. The number of NOTS points added to your record, if any, will depend on the specific violation charged and the point system used by the jurisdiction in question.
It's important to note that NOTS points are used to track and measure the driving record of a driver, and they may impact insurance rates and license status. It's always a good idea to familiarize yourself with the laws and regulations in your area and drive safely to reduce the risk of violations and penalties.
It is a system that is used to solve problems and interact with the environment
Variable
Computing System
Network
Computer
Answers
The term that encompasses asystem used to solve problems and interact with the environment is a "computing system."
Why is a computing system important?Technology has improved to the point where computer systems are employed by every sector to boost efficiency and remain ahead of their competition.
"A computing system is often made up of hardware components (such as computers and server s) and software components (such as operating systems and apps) that collaborate to execute tasks, analyze data, and interface with people or other systems.
It can include a variety ofdevices, networks, and computer resources to facilitate problem solving, data processing, communication, and other computational operations.
Learn more about computer at:
https://brainly.com/question/29892306
#SPJ1
true/false. the most common hybrid system is based on the diffie-hellman key exchange, which is a method for exchanging private keys using public-key encryption.
Answers
The given statement "The most common hybrid system is based on the diffie-hellman key exchange, which is a method for exchanging private keys using public-key encryption." is False because the most common hybrid system is based on RSA encryption.
The most common hybrid system is based on RSA encryption, which is a public-key encryption method for exchanging private keys. Diffie-Hellman key exchange, on the other hand, is a key exchange algorithm used to establish a shared secret between two parties over an insecure communications channel. To create secure communication between two parties, encryption, and decryption methods are used.
The RSA encryption algorithm is the most commonly used public-key encryption method. The RSA algorithm is named after its inventors, Ron Rivest, Adi Shamir, and Leonard Adleman. It is based on the difficulty of factoring large numbers. The security of RSA encryption is based on the fact that it is difficult to factor large numbers into their prime factors.
Know more about RSA encryption here :
https://brainly.com/question/27116296
#SPJ11
Discuss the major procedures that investigators must use in order to collect network trace evidence of computer-related crimes.
Answers
Answer:
The answer is below
Explanation:
The major procedures that investigators must use to collect network trace evidence of computer-related crimes include the following:
1. Establish appropriate guidelines to follow: before starting the actual investigation, all the legal procedures and instructions to follow must be clearly stated and shown to everybody involved in the investigation process.
2. Assess the Evidence: the investigators must assess all the available evidence by checking the computer through a specific means. The assessment includes checking of hard drives, email accounts, social networking sites, or similar digital prints that can be used as proof of the criminal activities
3. Acquire the Evidence: here the investigators must find an appropriate means of gathering the evidence formally and legally. This may involve the removal of any form of hardware such as hard drives, and software-related items that can be extracted.
4. Examine the Evidence: this involved examination of the acquired evidence, to determine if it can be used as proof or not. This involved analyzing the evidence to check if they correlate with the criminal activities under investigation. Some of the things to check include, date of formation of the evidence, the names attached to it, the routes those data were sent or received from, etc.
5. Prepare a report and document them appropriately: this involved the proper detailing and recording of the information derived from the evidence. It includes the time of evidence examination and methods used in examining them. Also, the means at which they acquired the evidence among others.
Which option describes a systematic error in measuring in the following scenario?
A nurse is performing a pre-assessment before a patient is seen by a physician.
The patient's weight is inaccurate due to the calibration of the scale.
O The patient's temperature changes during the pre-assessment.
o The nurse measures the patient's weight twice and observes two different measurements.
o The nurse estimates the patient's weight based on the increments on the scale.
UiT onroTION
Answers
Answer:
D - The patient’s weight is inaccurate due to the calibration of the scale.
Explanation:
if feel like it is but i'm not 100% sure, sorry if not right answer ( also taking the assignment )
The answer is:
The patient’s weight is inaccurate due to the calibration of the scale.Write the steps to enter records in Datasheet view
Answers
Answer:
Overview of How to Add Records to a Table in Datasheet View in Access
You can easily add records to a table in datasheet view in Access. In datasheet view in Microsoft Access, there is a blank row at the bottom of the table. This row also contains an asterisk (*) in the row selector box at its left end. This is the “New Record” row. When you add records to a table in datasheet view in Access, each new record is added to the bottom of the table in the “New Record” row.
To add records to a table in datasheet view in Access, click into this row and enter the new record. The asterisk will then change to a picture of a “pencil” as you do this. That lets you know which record you are currently editing. Another new “New Record” row also appears below the row where you are entering data.
After opening a table in datasheet view, you can quickly move to the “New Record” row. To do this, click the “New Record” button at the right end of the “Record Navigation” button group in the lower-left corner of the datasheet view. It is the button with the [►*] face. Your cursor will then automatically enter into that row. You can then enter the new record’s data to add records to a table in datasheet view in Access.
A picture showing how to add records to a table in datasheet view in Access.
Instructions on How to Add Records to a Table in Datasheet View in Access
To add records to a table in datasheet view in Access, open the desired table in datasheet view.
Click the “New Record” button at the right end of the record navigation button group. This button group appears in the lower-left corner of the datasheet view. It is the button with the arrow and asterisk [►*] on its face.
Then enter the information into the fields in the “New Record” row. It is the bottommost row in the datasheet view that displays the asterisk [*] at the left end of the row.
When you have finished entering the new record, you can move down to enter the next new record into the new row that has appeared.
Close the table when you are finished adding
A number is a palindrome if its reversal is the same as itself. Write a program ReverseNumber.java to do the following:
1. Define a method call reverse, which takes a 4-digit integer and returns an integer in reverse. For example, reverse(1234) should return 4321. (Hint: use / and % operator to separate the digits, not String functions)
2. In the main, take user input of a series of numbers, call reverse method each time and then determine if the number is a palindrome number, for example, 1221 is a palindrome number, but 1234 is not.
3. Enhance reverse method to work with any number, not just 4-digit number.
Answers
The reverse method takes an integer as input and reverses it by extracting the last digit using the modulus operator % and adding it to the reversed number after multiplying it by 10.
The Programimport java.util.Scanner;
public class ReverseNumber {
public static int reverse(int number) {
int reversedNumber = 0;
while (number != 0) {
int digit = number % 10;
reversedNumber = reversedNumber * 10 + digit;
number /= 10;
}
return reversedNumber;
}
public static boolean isPalindrome(int number) {
return number == reverse(number);
}
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
System.out.print("Enter a number: ");
int number = scanner.nextInt();
if (isPalindrome(number)) {
System.out.println(number + " is a palindrome number.");
} else {
System.out.println(number + " is not a palindrome number.");
}
}
}
Read more about Java program here:
https://brainly.com/question/26789430
#SPJ1
What will be the output of the following Python code?
>>>names = ['Amir', 'Bear', 'Charlton', 'Daman']
>>>print(names[-1][-1])
a. A
b. n
c. Error
d. Daman
Answers
Answer:
n
Explanation:
List is a data structure in Python that is used to hold multiple items. If we would like to access any item in a list, we may use the index. Index refers to the position of the item in a list and starts from 0. For example, names[0] refers to the first item, Amir, names[1] refers to the Bear in our list. We can also use negative index values. For example, names[-1] refers to the last item, Daman, names[-2] refers to Charlton in our list.
A list called names is initialized with four string variables and we would like to print the value of names[-1][-1].
We already said that names[-1] is the last item in our list. Then, the question turns out to print the 'Daman'[-1]. As we already said, the items are strings. Actually, string variables are kind of lists that consist of characters. That means, they can also be manipulated using index. So, 'Daman'[-1] would give us the last item, n, in our string, Daman.
how many nibbles make one kilobyte
Answers
Answer:
2000 nibbles
Explanation:
2000 nibbles is needed for 1 kilobyte
how to find tax rate using VLOOKUP in microsoft excel
Answers
To find a tax rate using VLOOKUP in Microsoft Excel, you would set up a table with tax brackets and corresponding rates, and then use the VLOOKUP function to match the income amount and retrieve the corresponding tax rate.
What is VLOOKUP?
When you need to find anything in a table or a range by row, use VLOOKUP. Look for the pricing of an automobile item by its part number, or locate an employee's name by their employee ID.
The VLOOKUP method requires three inputs, in this order: lookup value, table array, and column index number. The lookup value is the value for which you wish to locate matching data and must be in the lookup table's first column; it can be a value, a text string, or a cell reference.
Learn more about VLOOKUP:
https://brainly.com/question/30154536
#SPJ1
The ________ contains links to folders and files that Windows determines you access frequently or links that you have added.
Answers
Answer:
Quick access list
Explanation:
Normally in computers, quick access list is usually the first node in the navigation pane and it contains links to folders and files that you access frequently plus the ones that you add by yourself. Windows detects them.
Luke is setting up a wireless network at home and is adding several devices to the network. During the setup of his printer, which uses 802. 11g standard, he finds that he can't connect to the network. While troubleshooting the problem, he discovers that his printer is not compatible with the current wireless security protocol because it is an older version of hardware.
What wireless network security protocol will allow Luke to use the printer on his wireless network?
a. WPA
b. WEP
c. WPA2
d. WPA-PSK+WPA2-PSK
Answers
The wireless network security protocol that will allow Luke to use the printer on his wireless network is WEP. The correct answer is option b.
WEP (Wired Equivalent Privacy) is a security protocol that is used to secure wireless networks. It was introduced in 1999 and was widely used in the early days of wireless networking. However, it is an older version of hardware and is considered less secure than newer protocols such as WPA (Wi-Fi Protected Access) and WPA2 (Wi-Fi Protected Access 2).
Since Luke's printer is an older version of hardware, it is not compatible with the current wireless security protocol. Therefore, using WEP will allow Luke to use the printer on his wireless network.
Learn more about wireless network security:
brainly.com/question/30087160
#SPJ11
Which of the following steps to reproduce is grammatically correct: O App freeze in reopen The app freezes when reopened. Reopening Freezes the App. O The app will freeze, when reopen. O App crashing on Reopening
Answers
Grammatically correct: The app will freeze, when reopen.
Using when in sentenceIn simple terms, when is a conjunction for:
Two actions that are completed at the same time (two single actions at the same time) or one action that is performed immediately after another action is completed (one action immediately after another), Action in the past with a long duration. AgeWhen is one of the subordinate conjunction which is used to express a time relationship or as a time expression.
The subordinate conjunction is used in the subordinate clause (in this case it is called the time clause) to bridge the relationship with the main/independent clause. The combination between the time clause and the main clause is called a complex sentence.
Learn more about grammar at
https://brainly.com/question/2977084
#SPJ1
You replace an internal drive that is only used to backup data on a computer. Before you
install the case cover, you power on the computer and observe the disk drive lights are not
blinking. You suspect it may not be receiving power, but cannot find the power supply tester.
How can you quickly verify whether power is being supplied to the disk drive?
Answers
The way to quickly verify whether power is being supplied to the disk drive is through the use of a multimeter.
How do you check your power supply?There are different ways to know if power is entering your system. A person can be able to check the power supply on their computer by removing the side panel that pertains to its case.
Note that when a person bought any kind of rebuilt computer, you are able to likely check the power supply with the use of the computer's manual or by asking or contacting the manufacturer.
Therefore, based on the above, The way to quickly verify whether power is being supplied to the disk drive is through the use of a multimeter.
Learn more about multimeter from
https://brainly.com/question/5135212
#SPJ1
What computer part it this? Explain to get brainliest. People that don't explain, won't get it, but will get a thanks + a 5 star rate.

Answers
Answer:
That is a motherboard, a circuit board containing the main components (CPU, RAM, etc) of a computer. It contains connectors in which other circuit boards can be slotted into.
Explanation:
A motherboard is a specialized circuit board (a thin board containing a electrical circuit) used for containing major components of a computer and allowing the parts to be used in conjunction with each other. This is why you'll find a motherboard in a large variety of computers, from phones, to PC's and laptops.
Answer: Motherboard.
Explanation: it's the backbone of a computer, it ties all the computers components together.
As a high school student, what do you think is the advantage of someone who has knowledge about the basics of internet compared to those who have not yet experienced using it?
Answers
Answer:
For your future in your career, you will definitely have an upper hand and will be able to access and use more tools. But the person that has never used a computer before does not know what exactly they are missing. When they try to use a computer, they will struggle with simple task that now come naturally to you.
Explanation:
Referring to narrative section 6.4.1.1. "Orders Database" in your course's case narrative you will:
1. Utilizing Microsoft VISIO, you are to leverage the content within the prescribed narrative to develop an Entit
Relationship Diagram (ERD). Make use of the 'Crow's Foot Database Notation' template available within VISIC
1.1. You will be constructing the entities [Tables] found within the schemas associated with the first letter of
your last name.
Student Last Name
A-E
F-J
K-O
P-T
U-Z
1.2. Your ERD must include the following items:
All entities must be shown with their appropriate attributes and attribute values (variable type and
length where applicable)
All Primary keys and Foreign Keys must be properly marked
Differentiate between standard entities and intersection entities, utilize rounded corners on tables for
intersection tables
●
.
Schema
1 and 2 as identified in 6.4.1.1.
1 and 3 as identified in 6.4.1.1.
1 and 4 as identified in 6.4.1.1.
1 and 5 as identified in 6.4.1.1.
1 and 6 as identified in 6.4.1.1.
.
Answers
The following is a description of the entities and relationships in the ERD -
CustomersProductOrdersOrder Details How is this so?Customers is a standard entity that stores information about customers, such as their name, address,and phone number.Products is a standard entity that stores information about products, such as their name, description, and price.Orders is an intersection entity that stores information about orders, such as the customer who placed the order,the products that were ordered, andthe quantity of each product that was ordered.Order Details is an intersection entity that stores information about the details of each order,such as the order date, the shipping address, and the payment method.The relationships between the entities are as follows -
A Customer can place Orders.An Order can contain Products.A Product can be included inOrders.The primary keys and foreign keys are as follows -
The primary key for Customers is the Customer ID.The primary key for Products is the Product ID.The primary key for Orders is the Order ID.The foreign key for Orders is the Customer ID.The foreign key for Orders is theProduct ID.The foreign key for Order Details is the Order ID.The foreign key for Order Details is the Product IDLearn more about ERD at:
https://brainly.com/question/30391958
#SPJ1
You are asked to transfer a few confidential enterprise files using the file transfer protocol (FTP). For ensuring utmost security, which variant of FTP should you choose
Answers
Considering the situation described above, to ensure utmost security, the variant of FTP people should choose is SFTP.
What is SFTP?SFTP is the acronym for Secure File Transfer Protocol (SFTP). It functions through the Secure Shell (SSH) data stream to create a secure connection.
SFTP is generally known for providing excellent protection for file transfer.
Other types of FTPAnonymous FTPPassword Protected FTPFTP Secure (FTPS)FTP over explicit SSL/TLS (FTPES)Hence, in this case, it is case, it is concluded that the correct answerer is SFTP.
Learn more about file transfer protection here: https://brainly.com/question/17506968
Are AWS Cloud Consulting Services Worth The Investment?
Answers
AWS consulting services can help you with everything from developing a cloud migration strategy to optimizing your use of AWS once you're up and running.
And because AWS is constantly innovating, these services can help you keep up with the latest changes and ensure that you're getting the most out of your investment.
AWS consulting services let your business journey into the cloud seamlessly with certified AWS consultants. With decades worth of experience in designing and implementing robust solutions, they can help you define your needs while executing on them with expert execution from start to finish! AWS Cloud Implementation Strategy.
The goal of AWS consulting is to assist in planning AWS migration, design and aid in the implementation of AWS-based apps, as well as to avoid redundant cloud development and tenancy costs. Project feasibility assessment backed with the reports on anticipated Total Cost of Ownership and Return on Investment.
Learn more about AWS consulting, here:https://brainly.com/question/29708909
#SPJ1
Is it important to study information systems
Answers
Answer:
There is massive importance if you want to study information study.
It can help you understand the data, organize, and process the data, using which we can generate and share information.
Explanation:
It largely depends on your interest and requirement, but a better knowledge or clue about information systems may help analyze the data especially if you want to become a data scientist, machine learning, Artificial intelligence or deep learning, etc.
It can help you understand the data, organize, and process the data, using which we can generate and share information.
A great understanding of information systems may exponentially increase the productivity, growth, performance, and profit of the company.
Most Professions get exposed to information Systems no matter what their career objective is, as it may help in having better decision making based on the information they get through data.
So, yes!
There is a massive importance if you want to study information study.
of a
Which of these describes the result of running a
query?
a datasheet displaying records
bles
a field
an interface between the user and the
database
a summary of select data
DONE
Answers
Answer:
interface
Explanation:
(aka query thingy)
Answer:
A: a datasheet displaying records
Explanation:
I just did the Part 1 on EDGE2022 and it's 200% correct!
Also, heart and rate if you found this answer helpful!! :) (P.S It makes me feel good to know I helped someone today!!)

. Write a program to calculate the square of 20 by using a loop
that adds 20 to the accumulator 20 times.
Answers
The program to calculate the square of 20 by using a loop
that adds 20 to the accumulator 20 times is given:
The Programaccumulator = 0
for _ in range(20):
accumulator += 20
square_of_20 = accumulator
print(square_of_20)
Algorithm:
Initialize an accumulator variable to 0.
Start a loop that iterates 20 times.
Inside the loop, add 20 to the accumulator.
After the loop, the accumulator will hold the square of 20.
Output the value of the accumulator (square of 20).
Read more about algorithm here:
https://brainly.com/question/29674035
#SPJ1
This is science I just couldn’t find it

Answers
Answer:
69
Explanation:
It is 69 because it is the most for that degree.
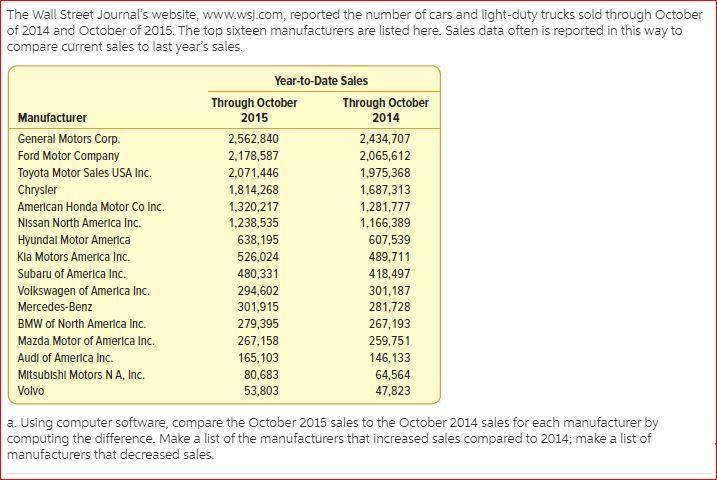
A furniture rentingstore rents severaltypes of furnituretocustomers.It charges a minimum fee for the first month. The store charges an additional fee every monthin excess of the first month. There is amaximum charge forany givenyear. Write a program that calculates and prints the chargefor a furniturerental.
Answers
Incomplete question. Attached is an image of the full question.
Explanation:
The best program to use is MS Excel. By using the Summation formula MS excel we can derive the difference in sales for the two years.

Write a single statement that assigns avg_sales with the average of num_sales1, num_sales2, and num_sales3. Sample output with inputs: 3 4 8 Average sales: 5.00
Answers
The statement that assigns avg_sales with the average of num_sales1, num_sales2, and num_sales3 is given below.
What is the statement that executes the above output?avg_scale = 0 num_scale1 = int(input()) num_scale2 = int(input()) num_scale3 = int(input()) avg_scale = (num_scale1+num_scale2+num_scale3)/3
print('Average scale: {:.2f}'.format(avg_scale))
What is a statement in programming?
A statement is a single line of code in computer programming that accomplishes a specified purpose.
A statement is shown by the following piece of computer code from the Perl programming language. $a = 3; In this example sentence, a variable ($a) is given the value "3," which is then saved as a string.
Learn more about statement:
https://brainly.com/question/16922594
#SPJ1
If you create a graph and later notice a mistake in the data, you can update the data and the graph will automatically update.
True or False
Answers
Answer:
false
Why?
you can't automatically update something. it takes time lots of time maybe 2 hrs or less or more but i could never.\
Help plz
Which of the following statements are true about cyberbullying:
1. Cyberbullying uses electronic communication to bully a person.
11. Cyberbullying is a crime in many states.
III. Instances of cyberbullying do not affect the digital footprint of the victim.
IV. Cyberbullying hurts real people even though we can't always see their reactions
online.
I and IV
O ll and III
O 1, 11, and IV
All of the above
Answers
The following statements are true about cyberbullying: Cyberbullying uses electronic communication to bully a person. Cyberbullying hurts real people even though we can't always see their reactions.
What is cyberbullying?The use of mobile phones, instant messaging, e-mail or social networking sites to intimidate or harass someone is known as cyberbullying.
The correct answer is "I and IV." Statement I is true because cyberbullying is defined as using electronic communication to bully a person.
Statement IV is also true because even though we may not be able to see the victim's reactions online, cyberbullying can still have real-life consequences and can hurt the victim emotionally or mentally.
Statement II is false because cyberbullying is a crime in many states, and statement III is also false because instances of cyberbullying can affect the victim's digital footprint.
Hence, the correct statements are "I and IV".
To learn more about cyberbullying click here:
https://brainly.com/question/8142675
#SPJ2
Marissa has recently accepted a job as a transcriptionist that will require several hours of typing a day. What are two pieces of advice you would give her to make sure her workstation is set up ergonomically? You need to answer the prompt in full to receive it.
You need to have at least five complete sentences.
You need to use proper grammar, capitalization, and punctuation.
Answers
Additionally, Marissa can take frequent breaks to stretch her hands, arms, and neck and perform exercises to prevent stiffness.
What is transcriptionist?
The field of transcription offers a variety of prospects and good income. An advanced transcriptionist makes between $25 and $30 per hour, while a transcriptionist normally makes around $19.02 per hour. If you labour 2.5 hours every day for 24 days, you could easily earn an average of $1141.2 per month at this pace.
requirements for transcribers:
diploma from high school.
There can be a need for a degree, an associate's degree, or other training.
knowledge of Express Scribe, and other programmes.
a quick typing speed and superior reading comprehension.
High professional standards and a strong work ethic.
An excellent second job for someone with additional time is transcription. Despite the fact that it's crucial to only take on tasks you can do in the allotted amount of time.
Read more about transcriptionist:
https://brainly.com/question/25703686
#SPJ1
In what way can an employee demonstrate commitment?
Answers
Answer:
Come to work on time ready to work. Always work above and beyond. ... Come to work on time, follow all rules, do not talk about people, and be positive get along with coworkers.
Explanation:
An employee can demonstrate commitment to their job and organization in several ways.
First and foremost, they show dedication and enthusiasm by consistently meeting deadlines, going above and beyond to achieve goals, and taking ownership of their responsibilities.
Being punctual and reliable also reflects commitment. Employees who actively participate in team efforts, support colleagues, and offer innovative ideas exhibit their dedication to the company's success.
Demonstrating a willingness to learn and grow by seeking additional training or taking on new challenges further showcases commitment.
Ultimately, a committed employee is driven by a genuine passion for their work, a strong work ethic, and a sense of loyalty to their organization's mission and values.
Know more about employee commitment:
https://brainly.com/question/34152205
#SPJ6
Next, Jamal wants to copy text from a Word document to the slide he just added. He outlines the steps to complete his task. Step 1: Select the text. Step 2: Click the Copy button. Step 3: Click the Paste button. Which step is missing? Where should this step be placed in Jamal’s outline?
Answers
Answer:place an insertion point/after step 2
Explanation:I just took the quiz
Answer:
place the insertion point, after step two
Explanation: