You work for a penetration testing consulting company. During an internal penetration test, you find that VNC is being used on the network, which violates your company's security policies. It was installed to maintain access by a malicious employee. Run a scan using nmap to discover open ports on host machines to find out which host machines are using port 5900 for VNC.
In this lab, your task is to complete the following:
Use Zenmap to scan for open ports running VNC. Use the table below to help you identify the computer.
Go to the suspect computer and uninstall VNC.
From the suspect computer, run netstat to verify the ports for VNC are closed.
Answers
Answer:
From the Favorites bar, open Terminal.
At the prompt, type ssh -X 192.168.0.251 and press Enter.
For the root password, type 1worm4b8 and press Enter.
You are now connected to Rogue1.
Type zenmap and press Enter to launch Zenmap remotely.
Zenmap is running on the remote computer, but you see the screen locally.
In the Command field, type nmap -p- 192.168.0.0/24.
Select Scan.
From the results, find the computers with ports open that make them vulnerable to attack.
In the top right, select Answer Questions.
Answers to Question:
192.168.0.10,
192.168.0.11,
192.168.0.14,
192.168.0.35
To complete this task, you would need to use nmap, a powerful network scanning tool, to identify which host machines on the network are using port 5900 for VNC. To do this, you can use Zenmap, which is a GUI frontend for nmap.
First, you would need to launch Zenmap and enter the IP range of the network you want to scan. Next, you would select the "Intense Scan" option from the Scan Profile dropdown menu, and then select the "VNC" option from the "Ping/Scan" tab. This will scan for open ports running VNC on all the host machines in the specified IP range.
Once the scan is complete, you can use the table provided to identify the computer(s) that are using port 5900 for VNC. Once you have identified the suspect computer, you can proceed to uninstall VNC from it.
To do this, you can go to the Control Panel of the suspect computer and select "Uninstall a Program." Locate the VNC software and uninstall it.
After uninstalling VNC, you can verify that the ports for VNC are closed by running netstat from the command line on the suspect computer. Netstat is a command-line tool that displays active network connections and their corresponding ports. If the ports for VNC are closed, they will not show up in the netstat output.
To know more about Intense Scan, click here:
https://brainly.com/question/30321389
#SPJ11
Related Questions
Does technology make us lazy? Explain. (Remember to support your
answer with citations and references)
Answers
The impact of technology on human laziness is a topic that has been widely debated and it is true to some extent.
Does technology make us lazy?Some argue it makes us lazy, while others say it can enhance productivity and efficiency.
Argument - technology makes us lazy. Advocates claim tech's conveniences can promote inactivity and a sedentary lifestyle. Tasks once done by hand can now be completed with machines, leading to possible over-reliance on technology and less physical activity, which causes health issues.
Tech improves productivity and efficiency. Tech revolutionized communication, info access, & task automation, enabling more accomplishment in less time.
Learn more about technology from
https://brainly.com/question/7788080
#SPJ1
Consider the following two code segments. Assume that the int variables m and n have been properly declared and initialized and are both greater than 0.
for (int i = 0; i < m * n; i++)
{
System.out.print("A");
}
for (int j = 1; j <= m; j++)
{
for (int k = 1; k < n; k++)
{
System.out.print("B");
}
}
Assume that the initial values of m and n are the same in code segment I as they are in code segment II. Which of the following correctly compares the number of times that "A" and "B" are printed when each code segment is executed?
Answers
Therefore, the number of times that "A" is printed is equal to the number of times that "B" is printed if and only if m * n = (m - 1) * n, which simplifies to m = 1.
In other words, if m is equal to 1, then the two code segments will print the same number of "A"s and "B"s. If m is greater than 1, then code segment I will print more "A"s than code segment II will print "B"s. If m is less than 1, then code segment II will print more "B"s than code segment I will print "A"s.
Which of the following procedures will enable you to sort your spreadsheet by city (Column K) in ascending order? Select all that apply.
Use the SORT function syntax: =SORT(A2:R210, K, TRUE)
Use the SORT function syntax: =SORT(A2:R210, 11, TRUE)
Select A2-R210, then use the drop-down menu to Sort Range by Column K from A to Z
Select A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z
Correct. To sort your spreadsheet by city in ascending order, you can use one of two methods. You can use the SORT function syntax =SORT(A2:R210, 11, TRUE)*. You can also select A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z.
Answers
It is to be noted that the option that would allow one to sort their spreadsheet is:
SORT function syntax =SORT(A2:R210, 11, TRUE)*. (Option B)A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z. (Option D).What does it mean to sort a spreadsheet?When sorting data in a spreadsheet, you may rearrange the data to rapidly discover values. Sorting a range or table of data on one or more columns of data is possible. You can, for example, rank personnel first by the department and then by last name.
Systematic representation is one of the advantages of sorting data. Sorting allows users to represent facts in a fairly methodical way that allows for precise display.
Better data understanding - when data is presented in a sorted and filtered manner, data decoding and understanding become very simple.
Learn more about spreadsheets:
https://brainly.com/question/26919847
#SPJ1
HELP ASAP!!!
What are some potential challenges that society will face given the digital revolution? You may want to think particularly of the news industry.
Answers
Femke went to a computer lab and connected her laptop to the WiFi network. She later received an email from the lab administrator warning that the WiFi network was in fact a rogue access point.
Which of the following could have occurred while she was connected to the rogue access point?
Answers
Femke may have experienced several consequences while connected to the rogue access point.
Could Femke have encountered any issues while connected to the rogue access point?When Femke connected her laptop to the rogue access point in the computer lab, she exposed herself to potential security risks. Rogue access points are unauthorized and can be set up by malicious actors to deceive users into connecting to them. Once connected, the attacker can intercept network traffic, steal sensitive information, and even launch various attacks on the connected devices.
The dangers of rogue access points, which can lead to unauthorized access and compromise the security of users and their devices. Attackers can eavesdrop on communications, perform man-in-the-middle attacks, and distribute malware. It is crucial to be vigilant when connecting to Wi-Fi networks and ensure they are authorized and secure.
Learn more about access point
brainly.com/question/29346507
#SPJ11
pls paanswer asap......

Answers
Answer:
Bro if you are really doing this on your phone or on a device look it up
Explanation:
Sorry for killing it, but dude, look it up on your phone, it doesn't take that long, it takes longer to wait for a response.
what is the use of numeric variable list any two numeric variable
Answers
Answer:
Numeric variables have data values that are recognized as numbers hence they can be sorted numerically or entered into arithmetic calculations.
Two types of numerical variables are: interval and ratio.
-An interval variable has values whose differences are interpretable but it does not have a true zero.
-A ratio variable is a variable with the features of interval variable and, additionally, whose any two values have meaningful ratio, making the operations of multiplication and division meaningful.
Explanation:
___ use a variety of approaches and systems to build their cloud systems, such as servers using distributive processing methods with data farms for storage.
Answers
Cloud providers use a variety of approaches and systems to build their cloud systems, such as servers using distributed processing methods with data farms for storage.
Cloud providers employ different technologies and architectural approaches to construct their cloud infrastructure. Distributed processing methods involve the use of multiple servers or nodes working together to handle computational tasks and distribute the workload efficiently across the system. This approach enables scalability, fault tolerance, and high availability.
Data farms, also known as data centers or server farms, are facilities that house a large number of servers and storage devices. These data farms provide the necessary infrastructure to store and manage vast amounts of data for cloud services. They are designed to ensure reliable data storage, data backup, and data redundancy, supporting the seamless operation of cloud-based applications and services.
Know more about Cloud providers here:
https://brainly.com/question/27960113
#SPJ11
In Python, if var1 = “Happy” and var2= “Birthday” and var3 = (var1+var2) *2, then var3 stores the string
A)“Happy BirthdayHappyBirthday”
B)“HappyHappyBirthday”
C)“HappyBirthdayHappyBirthdayHappyBirthday”
D)“HappyBirthdayBirthday”
Answers
Answer:
A
Explanation:
var3 is happy + birthday, ×2
l.e happy birthday happy birthday
Answer:
Your answer is A
Can speakers receive and send data?
Answers
Answer:
Depends.
Explanation:
If its a smart speaker, like Amazon Echo or Google Home, most likely yes. Especially since they have to communicate to other smart speakers if you have multiple. If you ask it questions, sometimes it pulls from its data banks to help answer it more accurately.
Answer:
CNCBN C FGB DHFJ NSJD
Explanation:
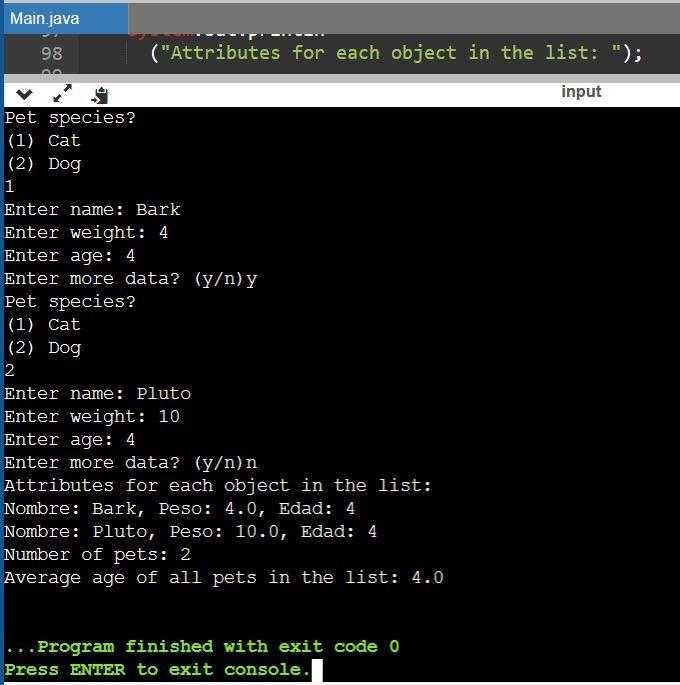
In an earlier assignment you modeled an inheritance hierarchy for dog and cat pets. You can reuse the code for that hierarchy in this assignment. Write a program that prompts the user to enter data (name, weight, age) for several Dog and Cat objects and stores the objects in an array list. The program should display the attributes for each object in the list, and then calculate and display the average age of all pets in the list using a method as indicated below:
public static double calculateAverage( ArrayList list )
{
... provide missing code ...
}
previous code
chihuahua
public class Chihuahua extends Dog
{
public void bark()
{
System.out.println("Bow wow");
}
}
dog
public class Dog
{
private String name;
private double weight;
private int age;
public String getname(String n)
{
name = n;
return n;
}
public double getweight(double w)
{
weight = w;
return w;
}
public int getage(int a)
{
age = a;
return a;
}
public void bark()
{
}
}
import java.util.Scanner;
public class DogCatTest
{
public static void main( String [] args)
{
Scanner scan = new Scanner(System.in);
System.out.println("Enter name");
String name = scan.nextLine();
System.out.println("Enter weight");
double weight = scan.nextDouble();
System.out.println("Enter age");
int age = scan.nextInt();
Dog [] dogCollection = { new Chihuahua(), new GoldenRetriever()};
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getname(name);
System.out.println(name);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getweight(weight);
System.out.println(weight);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].getage(age);
System.out.println(age);
for( int i = 0; i < dogCollection.length; i++ )
dogCollection[ i ].bark();
System.out.println("Enter name");
String cname = scan.nextLine();
System.out.println("Enter weight");
double cweight = scan.nextDouble();
System.out.println("Enter age");
int cage = scan.nextInt();
Cat1 [] catCollection = { new SiameseCat(), new SiberianCat() };
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getname(cname);
System.out.println(cname);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getweight(cweight);
System.out.println(cweight);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].getage(cage);
System.out.println(cage);
for( int i = 0; i < catCollection.length; i++ )
catCollection[ i ].meow();
}
}
public class GoldenRetriever extends Dog
{
public void bark()
{
System.out.println("Bow wow");
}
}
public class SiameseCat extends Cat1
{
public void meow()
{
System.out.println("Meow");
}
}
public class SiberianCat extends Cat1
{
public void meow()
{
System.out.println("Meow");
}
}
public class Cat1
{
private String name;
private double weight;
private int age;
public String getname(String n)
{
name = n;
return n;
}
public double getweight(double w)
{
weight = w;
return w;
}
public int getage(int a)
{
age = a;
return a;
}
public void meow()
{
}
}
Answers
Java program that shows the use of inheritance hierarchy, the code reuses the attributes of the class objects.
Importance of applying inheritance:In this case of pets (dogs and cats), applying inheritance allows a much shorter and more structured code. Also, reusable since we can add classes of other pets such as birds, rabbits, etc., all of them also belonging to the Pet superclass.
Reserved words in a java code that enforces inheritance:extendsprotectedSuperHere is an example:
Java codeimport java. io.*;
import java.util.ArrayList;
import java.io.BufferedReader;
public class Main
{
// ArrayList of Pet objetspublic static ArrayList < Pets > arraypets = new ArrayList < Pets > ();
public static void main (String args[]) throws IOException
{
BufferedReader data =
new BufferedReader (new InputStreamReader (System. in));
//Define variablesString aws;
String str;
double w;
String n;
int a;
double average;
do
{
//Data entry System.out.println ("Pet species? ");System.out.println ("(1) Cat ");
System.out.println ("(2) Dog ");
aws = data.readLine ();
System.out.print ("Enter name: ");
n = data.readLine ();
System.out.print ("Enter weight: ");
str = data.readLine ();
w = Double.valueOf (str);
System.out.print ("Enter age: ");
str = data.readLine ();
a = Integer.valueOf (str);
if (aws.equals ("1"))
{
Cat cat = new Cat (n, w, a);
arraypets.add (cat);
average = cat.averageAges (a);
}
else
{
Dog dog = new Dog (n, w, a);
arraypets.add (dog);
average = dog.averageAges (a);
}
System.out.print ("Enter more data? (y/n)");
aws = data.readLine ();
aws = aws.toLowerCase ();
}
while (!aws.equals ("n"));
//Calculate average of pets ageaverage = average / arraypets.size ();
average = Math.round (average * 100.0) / 100.0;
// OutputSystem.out.println ("Attributes for each object in the list: ");
for (Pets arraypet:arraypets)
{
System.out.println (arraypet);
}
System.out.println ("Number of pets: " + arraypets.size ());
System.out.println ("Average age of all pets in the list: " + average);
}
}
class Pets
{
protected String Name;
protected double Weight;
protected int Age;
public Pets ()
{
}
public Pets (String name, double weight, int age)
{
this.Name = name;
this.Weight = weight;
this.Age = age;
}
//Returning values formatted by tostring methodpublic String toString ()
{
return "Nombre: " + this.Name + ", Peso: " + this.Weight + ", Edad: " +
this.Age;
}
public void CalculateAverage ()
{
}
}
class Dog extends Pets
{
public Dog ()
{
super ();
}
public Dog (String name, double weight, int age)
{
super (name, weight, age);
}
//Adding the ages of the pets double averageAges (double a){
a += a;
return a;
}
}
class Cat extends Pets
{
public Cat ()
{
super ();
}
public Cat (String name, double weight, int age)
{
super (name, weight, age);
}
//Adding the ages of the petsdouble averageAges (double a)
{
a += a;
return a;
}
}
To learn more about inheritance hierarchy in java see: https://brainly.com/question/15700365
#SPJ4


You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
what is the problem here

Answers
Answer:
I think ...............
In comparison with a flat file system, _____ in a database.
Answers
In comparison with a flat file system,data organization in a database.
What is the database?A database is an organized collection of structured data, generally stored and accessed electronically from a computer system. It is the collection of schemas, tables, queries, reports, views, and other objects. Database systems are used to store and manage large amounts of data. They can provide quick and easy access to data for applications, as well as ensuring data integrity and accuracy. Databases are used for a variety of purposes, including data warehousing, e-commerce, online transaction processing, data mining, and more.
To learn more about database
https://brainly.com/question/24027204
#SPJ1
jiang is a network technician. he is programming a web server to provide clients with dynamically produced web content in real time based on several attributes that the connecting user enters. this includes any forms the user may fill out. martha is the cybersecurity chief. she says that the technology jiang is using could expose sensitive customer data to hackers if it were ever accessed. what web server technology is jiang using?
Answers
Jiang is using server-side scripting technology to produce dynamically generated web content in real-time based on the attributes that the connecting user enters, including any forms the user may fill out. This allows for a more personalized and interactive web experience for the user.
However, Martha, the cybersecurity chief, is concerned that this technology could expose sensitive customer data to hackers if it were ever accessed. Server-side scripting involves running scripts on the web server to generate dynamic web pages that are sent to the user's browser. This means that the user's data is processed and stored on the server, which could potentially be vulnerable to attacks if proper security measures are not in place. It is important for Jiang to ensure that the web server is configured securely and that data encryption and access controls are implemented to prevent unauthorized access to sensitive information. Additionally, regular security audits and vulnerability scans should be conducted to identify and address any potential weaknesses in the system.
learn more about data encryption here:
https://brainly.com/question/28283722
#SPJ11
What methods do you use when researching a complicated or difficult subject? What tools are most useful to narrowing down and validating your research? Explain your answers.
Answers
What does AutoCAD stands for?
Answers
Answer: it is comprised of 2 words Auto and CAD. AUTO stands here for AUTODESK ,an american company (parent company of autocad) CAD stands here for computer aided drafting or design as this software is used mainly for drafting but also has some designing features.
I hope it helps if It does can you please mark me as Brainliest!
Auto computer-aided design.
Complete the missing part of the line to allow you to read the contents of the file.
inFile = ____ ('pets.txt','r')
Answers
Answer: Sorry I’m late but the answer is open
Explanation: Edge 2021
The missing part of the line allows you to read the contents of the file. inFile = Open ('pets.txt','r').
What is the file format?The term file format refers to that, A standard way the information is encoded for storage in a computer file. It specifies how bits are used to encode information in a digital storage medium. File formats may be either proprietary or free.
The file format is the structure of that file, Which runs a program and displays the contents. As there are many examples like a Microsoft Word document saved in the. DOC file format is best viewed in Microsoft Word. Even if another program can open the file.
Therefore, By the File format allows you to read content and can open up the file format.
Learn more about file format here:
https://brainly.com/question/1856005
#SPJ2
The file has just been opened so the current position is at beginning of the first block The file descriptor resides in memory • Only a single data block can be ...
Answers
When a file is opened, the current position is typically set at the beginning of the first block, meaning that any subsequent read or write operations will start from this point.
The file descriptor, which contains information about the file, resides in memory. When working with a file system that allows only a single data block to be read or written at a time, you would need to sequentially access each block to read or modify the file content.
It seems like you are referring to a file system or a file being accessed by a program. When a file is opened, the current position is typically set to the beginning of the file or the first block of data in the file. This is because the program needs to start reading or writing data from the beginning before moving on to other parts of the file.
Additionally, it seems like there is a file descriptor involved, which is a data structure that contains information about the file being accessed. The file descriptor is stored in memory so that the program can access it easily and efficiently.
It's also mentioned that only a single data block can be accessed at a time. This means that the program needs to read or write one block of data before moving on to the next block. This is a common limitation of file systems, and it's important for programs to handle this properly to avoid errors or data corruption.
Learn more about file here:
https://brainly.com/question/18241798
#SPJ11
miriam is a network administrator. she would like to use a wireless authentication technology similar to that found in hotels where users are redirected to a webpage when they connect to the network. what technology should she deploy?
Answers
The technology she should deploy is a captive portal.
What do you mean by technology?
Technology is the application of knowledge to achieve practical goals in a predictable and repeatable manner. The term technology can also refer to the outcome of such an undertaking. Technology is widely used in medical, science, industry, communication, transportation, and everyday life. Physical objects such as utensils or machinery are examples of technologies, as are intangible instruments such as software. Many technological advances have resulted in societal shifts. The earliest known technology is the stone tool, which was employed in the prehistoric past, followed by fire use, which led to the development of the human brain and language throughout the Ice Age.
To learn more about technology
https://brainly.com/question/25110079
#SPJ4
power point cannot use

Answers
is copying legally purchased files to and from the cloud a fair use? if yes, explain how? if not, why not?
Answers
Whether copying legally purchased files to and from the cloud is considered "fair use" depends on the specific circumstances and applicable laws and the jurisdiction in which you are located.
In general, fair use is a doctrine in U.S. copyright law that allows for limited use of copyrighted material without the owner's permission. The purpose of the doctrine is to balance the interests of copyright owners with the interests of society as a whole. Fair use is determined on a case-by-case basis, taking into consideration four factors:
The purpose and character of the use, including whether it is commercial or non-commercial in nature.The nature of the copyrighted work.The amount and substantiality of the portion used in relation to the copyrighted work as a whole.The effect of the use upon the potential market for or value of the copyrighted work.It's important to keep in mind that while the fair use doctrine provides some flexibility, it is not an absolute right and can be difficult to interpret. As such, if you have any doubts about whether your use of copyrighted material is a fair use, it's best to consult with a qualified attorney.
Learn more about copyright here: https://brainly.com/question/357686
#SPJ4
for which of the grids does the program correctly move the robot to the gray square? responses grid i only grid i only grid ii only grid ii only both grid i and grid ii both grid i and grid ii neither grid i nor grid ii
Answers
Since both Grid I and Grid II correctly move the robot to the gray square, the correct answer is "both grid I and grid II."
To determine which grid correctly moves the robot to the gray square, we need to analyze the given options and compare them with the conditions provided.
Grid I: If the robot starts at the green square and moves left, up, right, and up again, it will end up at the gray square. So,
Grid I correctly moves the robot to the gray square.
Grid II: If the robot starts at the green square and moves right, up, left, and up again, it will end up at the gray square.
The Grid II also correctly moves the robot to the gray square.
To know more about square visit:-
https://brainly.com/question/14198272
#SPJ11
s Give the SQL statement to display the number of trips that originate in Vermont (VT) or Connecticut (CT)?? SELECT Count(TripName) FROM Trip WHERE State="VT OR State
Answer 1: COUNT(TripName) Answer 2: State='VTOR State='CT Partial
Answers
COUNT(Trip Name) is SQL statement to display the number of trips that originate in Vermont (VT) or Connecticut (CT).
What is SQL statement ?
An SQL statement is a set of instructions that properly compiles and includes identifiers, parameters, variables, names, data types, and SQL reserved words. If a Begin Transaction command does not define the beginning of a transaction, Analysis Services constructs an implicit transaction for a SQL query.
A database table's records are retrieved using a SQL SELECT statement in accordance with clauses (such FROM and WHERE) that define criteria. As for the syntax: the following query: SELECT column1, column2 FROM table1, table2 WHERE column2='value';
A computerised maintenance management system, or CMMS, is software that centralises maintenance data and streamlines maintenance procedures. It helps to maximise the efficiency and usability of tangible assets including machinery, infrastructure for plants, communications, and other assets.
Read more about SQL statement:
https://brainly.com/question/30175580
#SPJ1
What happens at the end of each iteration of the repeat loop in this code?
A. The program pauses for 2 seconds.
B. The shark's position on the screen changes.
C. The number of sharks increases
D. The shark follows the fish at a speed of 2000

Answers
Answer:
B. The shark's position on the screen changes.
Roger wants to give semantic meaning to the contact information, which is at the bottom of the web page. To do this he will use a footer element as a ______ of the contact information.
Answers
Answer:
Parent
Explanation:
HTML is an acronym for hypertext markup language and it is a standard programming language which is used for designing, developing and creating web pages.
Generally, all HTML documents are divided into two (2) main parts; body and head. The head contains information such as version of HTML, title of a page, metadata, link to custom favicons and CSS etc. The body of a HTML document contains the contents or informations that a web page displays.
In this scenario, Roger wants to give semantic meaning (an element conveying informations about the type of content contained within an opening and closing tag) to a contact information placed at the bottom of a webpage. Thus, in order to do this, he should use a footer element as a parent of the contact information and as such all instance variables that have been used or declared in the footer class (superclass) would be present in its contact information (subclass object).
PLEASE HELPPP!!! QBASIC WORK!
Write a program that asks a user to input length and breadth of a room in feet. This program displays message ‘Big room’ if the area of the room is more than or equal to 250 sq. ft otherwise it displays ‘Small room’.
Answers
Answer:
INPUT "Input Length: ";LENGTH
INPUT "Input Width: ";WIDTH
AREA = WIDTH*LENGTH
IF AREA >= 250 THEN PRINT "Big room"
IF AREA < 250 THEN PRINT "Small room"
Explanation:
A program executes 15 billion instructions. You are running this program in two systems: System A: has a processor with 3 GHz and an average CPI of 2.0 System B: has an average CPI 1.2 and execution time is 1.5 X more than system A. What is the clock speed of processor in system B.
Answers
Answer:
Clock speed of B = 7.5 GHz
Given:
Processor speed of A = 3 GHz
Average CPI of A = 2
Average CPI of B = 1.2
Execution time of B is 1.5 times then A
Find:
Clock speed of B
Computation:
Execution time = CPI × Processor speed × Instructions
Execution time of B = 1.5[Execution time of A]
1.2 × Clock speed of B[15 billion] = 1.5[2 × 3][15 billion]
Clock speed of B = 7.5 GHz
In designing the interior of a physical fitness center, Sybil pays attention to sight lines and the arrangement of rooms and equipment to avoid the fishbowl effect common to such structures. She wants to give people working out a sense of privacy and isolation. Accordingly, she designs the center’s workout areas to have lots of short walls and angles to reduce the number of people visible in any given direction. In reviewing her plans, the client is dismayed. What do you predict are potential problems with Sybil’s design? (Select all that apply.)
The complicated nature of Sybil’s design means that she is probably in violation of numerous codes governing the construction of such structures.
It would be impossible to have fitness classes because the trainer and the class members wouldn’t be able to see each other as they work out.
The lack of sight lines that can encompass entire areas means lots of hidden corners that can create safety and security concerns.
The labyrinth effect of so many short walls and angles likely means that the facility doesn’t make effective use of natural light coming in from outside.
Answers
Answer:
The potential problems with Sybil's design are;
1) Due to the complicated nature of Sybil's design means that she is probably in violation of numerous codes governing the construction of such structures
2) It would be impossible to have fitness classes because the trainer and the class members wouldn't be able to see each other as they work out
3) The lack of sight lines that can encompass entire areas means lots of hidden corners that can create safety and security concerns
4) The labyrinth of so many short walls and angles likely means that the facility doesn't make effective use of natural light coming in from outside
Explanation:
The design considerations for a fitness center includes
1) Provision of adequate space for circulation
2) The sizes of the interior should be varied to avoid the feeling of being inside a big box
3) Allow ample access to natural light
4) Visibility of activity areas to increase interest
5) Ensure that likely dangerous spaces are visible
6) Avoid the creation of dark or hidden corners
Therefore
1) There are likely probabilities that Sybil's design could be in violation of federal and state codes for building similar structures
2) There will be reduced visibility of the trainer
3) Hidden areas formed, due to lack of visibility can be a source of concern for safety
4) There could be limited access for natural light within the facility
what troubleshooting step should shahid do if he has been hibernating his machine every day for several weeks
Answers
It's not possible for me to provide specific troubleshooting advice without more context about the issues Shahid is experiencing with his machine.
Some general steps that Shahid could try to troubleshoot problems with his machine include:
Restarting the machine: Sometimes, restarting the machine can resolve issues that may have occurred while the machine was in use.Checking for and installing updates: Shahid should check for updates for his operating system and any installed software and install any available updates. This can help fix bugs and improve the stability and performance of the machine.Scanning for malware: Shahid should run a malware scan to check for and remove any malicious software that may be causing problems on his machine.Checking for hardware issues: Shahid should check for any hardware issues that may be causing problems with his machine. This could include checking for loose cables or damaged hardware components.Seeking technical support: If Shahid is unable to resolve the issues with his machine on his own, he may need to seek technical support from a professional. This could include contacting the manufacturer of his machine or a qualified repair technician.
It's also worth noting that regularly hibernating a machine may not be necessary, and there could be other ways to conserve energy and extend the battery life of the machine. Shahid may want to consider alternative power-saving strategies, such as adjusting the power settings or using a power management tool.
To know more about troubleshooting, visit: https://brainly.com/question/14394407
#SPJ4