assume you have been asked to develop an algorithm to determine the total cost for parking passes. please draw the flowchart with variable list based on the information below.
Answers
Based on the information provided, I cannot draw a flowchart, but I can describe the steps to create an algorithm for determining the total cost for parking passes.
1. List the variables: Let the variables be 'numberOfPasses' for the number of parking passes, 'costPerPass' for the cost of each parking pass, and 'totalCost' for the total cost of the parking passes.2. Input the number of parking passes: Ask the user to input the number of parking passes they want to purchase and store the value in the variable 'numberOfPasses'.
3. Input the cost per parking pass: Ask the user to input the cost of each parking pass and store the value in the variable 'costPerPass'.4. Calculate the total cost: Multiply 'numberOfPasses' by 'costPerPass' and store the result in the variable 'totalCost'. 5. Output the total cost: Display the value of 'totalCost' to the user.
To know more about flowchart visit:
https://brainly.com/question/29317974
#SPJ11
Related Questions
Please help, this question is from plato.
What is the purpose of the domain name?
The domain name: (.net , .com , org , .gov)
is an example of a service provider. The domain name .gov.nz is an example of a (New york , New Zealand, news, commercial)
government website.
Answers
Answer:
New Zealand government
Explanation:
Answer:
.net is for service providers and .gov.nz is for new Zealand governement
Explanation:
6. when a program is finished using a file, it should do this. a. erase the file b. close the file c. throw an exception d. reset the read position 17. this class allows you to use the print and println methods to write data to a file. a. file b. filereader c. outputfile d. printwriter 18. this class allows you to read a line from a file. a. filewriter b. scanner c. inputfile d. filereader 19. true or false: the while loop is a pretest loop. 20. true or false: the do-while loop is a pretest loop. 21. true or false: the for loop is a posttest loop. 22. true or false: it is not necessary to initialize accumulator variables. 23. true or false: one limitation of the for loop is that only one variable may be initialized in the initialization expression. 24. true or false: a variable may be defined in the initialization expression of the for loop. 25. true or false: in a nested loop, the inner loop goes through all of its iterations for every iteration of the outer loop. 26. true or false: to calculate the total number of iterations of a nested loop, add the number of iterations of all the loops.
Answers
Answer:
16. close the file
17. Output file
18. scanner
19. true
20. false
21. false
22. false
23. false
24. true
25. true
26. false
Explanation:
Hope it helps!
A popular game allows for in-app purchases to acquire extra lives in the game. When a player purchases the extra lives, the number of lives is written to a configuration file on the gamer's phone. A hacker loves the game but hates having to buy lives all the time, so they developed an exploit that allows a player to purchase 1 life for $0.99 and then modifies the content of the configuration file to claim 100 lives were purchased before the application reading the number of lives purchased from the file. Which of the following type of vulnerabilities did the hacker exploit?
a. Sensitive data exposure.
b. Dereferencing.
c. Broken authentication.
d. Race condition.
Answers
Based on the fact that the hacker's actions are done before the application reading of the lives purchased, this is d. Race condition.
What is a race condition?This is when certain processes in an application depend on the timing of a a previous process or event. The flow of information can then be intercepted before the process completes.
This is what the hacker did here by accessing the application to change the number of lives purchased before the application read the number of lives purchased.
In conclusion, option D is correct.
Find out more on the race condition at https://brainly.com/question/13445523.
you plan to deploy the following azure web apps: webapp1, that uses the .net 6 runtime stack webapp2, that uses the asp.net v4.8 runtime stack webapp3, that uses the java 17 runtime stack webapp4, that uses the php 8.0 runtime stack you need to create the app service plans for the web apps. what is the minimum number of app service plans that should be created?
Answers
Since you need to create the App Service plans for the web apps, the minimum number of App Service plans that must be created is option A-1.
How does Azure webapp work?Without needing to deploy, set up, and maintain your own Azure VMs, you may create an app in Azure using the platform offered by Azure Web Apps. The ASP.NET, PHP, Node. js, and Python may all be used to create web applications. Additionally, they incorporate well-known coding environments like GitHub and Visual Studio.
Microsoft developed and maintains Azure Web Apps, a platform for hosting websites based on cloud computing. It is a platform as a service that enables the publishing of Web apps using several frameworks and different programming languages, including proprietary ones from Microsoft.
Therefore, You can support up to 10 Web Apps by creating one App Service Plan. Any additional use of the other resources is unnecessary and not specified as a prerequisite.
Learn more about azure web apps from
https://brainly.com/question/28813133
#SPJ1
See full question below
You plan to deploy the following Azure web apps:
WebApp1, which uses the .NET 5 runtime stack
WebApp2, which uses the ASP.NET V4.8 runtime stack
WebApp3, which uses the Java 11 runtime stack
WebApp4, which uses the PHP 8.0 runtime stack
You need to create the App Service plans for the web apps.
What is the minimum number of App Service plans that must be created?
A-1
B-2
C-3
D-4
Casting is one of the oldest known manufacturing processes.
True or false
Answers
what utility should always be used in order to delete checkpoints?
Answers
In order to delete checkpoints, we should always use Remove-VMSnapshot utility. This utility is used to delete a checkpoint, which is also known as a snapshot in Hyper-V virtual machines. When a snapshot is created, the VM state is captured in a single file on the host system and can be used to revert the VM to a previous state if needed.
However, it is not recommended to use snapshots as a backup solution, as it can lead to performance degradation and disk space usage. Instead, it is recommended to use a proper backup solution to backup virtual machines. In order to use the Remove-VM Snapshot utility.
Open Power Shell with Administrator privileges. Type the following command to list all snapshots for a particular virtual machine :Get-VM Snapshot -VM Name "Virtual Machine Name"3. Once you have identified the snapshot you want to remove, use the following command to delete the snapshot.
To know more about checkpoints visit:
https://brainly.com/question/2110439
#SPJ11
In this exercise you will define Language Four, an extension of Language Three. Here is a sample program in Language Four, showing all the new constructs: let val fact = fn x > if x<2 then x else x * fact (x-1) in fact 5 end
Answers
Language Four is an extension of Language Three and introduces new constructs to the programming language. The sample program in Language Four illustrates the use of the new constructs.
The program defines a function called "fact" that takes a parameter "x" and calculates the factorial of that parameter. The function checks if the value of "x" is less than 2. If it is, then it returns the value of "x". Otherwise, it multiplies "x" by the result of the "fact" function called with "x-1" as the parameter.
The "let" keyword is used to define variables within the program. In this case, the variable "fact" is defined to hold the function definition. The "fn" keyword is used to define anonymous functions, which in this case is the parameter for "val". The ">" symbol is used to indicate a function that takes an argument.
In conclusion, Language Four introduces new constructs that enhance the functionality of Language Three. The sample program showcases the use of these new constructs in a factorial function definition.
To know more about program visit:
https://brainly.com/question/30613605
#SPJ11
What value is displayed as a result of executing the code segment?

Answers
Answer:
A: 3
Explanation:
The MOD operator is used to calculate the remainder of dividing two numbers, so by the end of this operation, we are adding the MODs of each integer in this list, because this program ends once each integer in list has gone through the steps, and the result of calculating the MOD of each integer is then added back because of the third step. So it should look like this: (4 MOD 2) + (2 MOD 2)...(1 MOD 2) and the result of adding these values should then result in 3.
The value which is displayed as a result of executing the code segment is equal to: A. 3.
What is MOD?MOD is an abbreviation for modulo operation and it can be defined as a mathematical technique that is used in computer science to determine the remainder of an arithmetic operation such as the division of two numbers.
Based on the code segment, the value which is displayed as a result of executing the modulo operation would be equal to 3 at the end of the iteration or operation.
Read more on computer codes here: brainly.com/question/25619349
https://soap2day.to/ free movies
Answers
Answer:
why is everyone sending links
Which of the following is used to store digital assets in wcm?
a) DAM
b) File
c) Database
d) All the options mentioned
Answers
The correct answer is option a) DAM (Digital Asset Management). DAM is specifically designed for storing and managing digital assets in Web Content Management (WCM) systems.
In the context of Web Content Management (WCM) systems, the most appropriate option for storing digital assets is a Digital Asset Management (DAM) solution, represented by option a).
DAM systems are specifically designed to organize, store, and manage digital assets such as images, videos, documents, and audio files. They provide functionalities for metadata management, versioning, search, retrieval, and distribution of digital assets.
While options b) (File) and c) (Database) can be used to store digital assets, they do not offer the specialized features and capabilities provided by a dedicated DAM solution. Storing digital assets simply as files or within a database may lack the robustness and efficiency required for effective asset management within a WCM environment.
Therefore, the most appropriate and effective choice for storing digital assets in WCM systems is to utilize a DAM solution, making option a) the correct answer. DAM systems provide the necessary tools and infrastructure to optimize the management and utilization of digital assets within the context of web content and online publishing.
Learn more about Web Content Management here:
https://brainly.com/question/15285487
#SPJ11
what is LATEX ?
create a latex command
Answers
Latex is a software used for writing daily life issue like integrations,fractions ,limits .
Lets see an example
\(\\ \bull\tt\longmapsto \displaystyle{\int}vdx\)
\(\\ \bull\tt\longmapsto \displaystyle{\lim_{x\to 0}}\)
true or false? mobile application management (mam) software often provides remote control to allow an administrator to take control of the phone.
Answers
You can control your business data on Windows computers and personal iOS and Android devices used by your customers with mobile application management.
What is versatile application the board programming?Software known as mobile application management (MAM) provides end users with IT control over enterprise applications on their personal and business smartphones and tablets. MAM programming permits IT heads to apply and uphold corporate arrangements on versatile applications and cutoff the sharing of corporate information among applications.
MAM safeguards data within appropriate applications. All data in university-owned applications is encrypted automatically when MAM is installed. After that, the encrypted data cannot be accessed by unauthorized users if a mobile device is stolen or lost.
Learn more about mobile application management here:
https://brainly.com/question/26304130
#SPJ1
a data analyst writes a query that asks a database to return only distinct values in a specified range, rather than including repeating values. which function do they use?
Answers
A data analyst writes a query that asks a database to return only distinct values in a specified range, rather than including repeating values using COUNT DISTINCT function.
Moreover, Data analysts use SQL to manipulate data, understand data, and access, read, and analyze data before storing it in a database. Metadata enables analysts to unlock meaning in Big Data. Ultimately, it increases the value of an organization's data resources by enabling data to be identified, discovered, and connected across the enterprise. Without metadata, much Big Data is unusable or unmanageable.
You can learn more about this at:
https://brainly.com/question/29341430#SPJ4
How can edge computing be used to increase sustainability
Answers
Edge computing be used to increase sustainability With Edge Computing the number of records traversing the network can be reduced greatly, freeing up bandwidth.
How is part computing sustainable?Data centers devour an expected 2 hundred terawatt-hours (TWh) of power every year–extra than the power intake of a few countries. They additionally produce an expected 2% of all worldwide CO2 emissions. Edge Computing reduces network site visitors and records centre usage.
Data centres devour an expected 200 terawatt-hours (TWh) of power every year–extra than the power intake of a few countries. They additionally produce an expected 2% of all worldwide CO2 emissions.
Read more about the sustainability:
https://brainly.com/question/25350238
#SPJ1
what is the definition of computer science procedural abstraction
Answers
Computer Science Procedural Abstraction is a process of simplifying a complex system or problem by breaking it down into smaller parts that can be understood and solved more easily.
What is Computer Science ?Computer Science is the study of the theory, experimentation and engineering that form the basis for the design and use of computers. It is a field of study that encompasses the development of computer hardware, software and networks. It also includes the design and implementation of algorithms and systems for processing, storing, exchanging and manipulating information.
This abstraction process is used to reduce a problem to its essential elements, allowing it to be solved faster and more efficiently. It is also used to make programming easier, by breaking down complex tasks into simpler, more manageable components. This abstraction process allows programmers to focus on the problem at hand, rather than having to worry about the details of how to implement it.
To learn more about Computer Science
https://brainly.com/question/20837448
#SPJ4
You carried out a PERT analysis of a very large activity-event network using only slightly skewed or symmetric beta distribution models for the activity durations. Your analysis yields a mean duration of 56.2 time units for the critical path with a variance of 3.4. What is your best estimate of the probability of successful project completion in 57 time units or less? Provide your answer as a number between 0 and 1 with 3 decimals (3 digits after the decimal point, for example: 0.123).
Answers
PERT (Program Evaluation and Review Technique) is a network analysis technique commonly used in project management.
It is particularly useful when there is a high level of uncertainty surrounding the duration of individual project activities. PERT uses probabilistic time estimates, which are duration estimates based on using optimistic, most likely, and pessimistic estimates of activity durations, or a three-point estimate.
These estimates help to identify the likelihood of meeting project deadlines and can assist project managers in developing effective project schedules and resource allocation plans. Overall, PERT is an important tool for managing complex projects with uncertain activity durations.
To know more about project management, refer to the link:
brainly.com/question/4475646#
#SPJ4
Can't find the right year for this. (Attachment)

Answers
Interactive sites where users write about personal topics and comment to a threaded discussion are called?
A. chat rooms.
B. networking sites.
C. forums
D. messaging sites.
Answers
Answer:
C. forums
Explanation:
Forums are internet sites where users can meet to discuss different topics through the use of messages thereby forming chat rooms. An internet forum can be in form of a question and answer site. Most websites have internet forums where users can meet and discuss or ask questions. Sometimes there may be moderators that ensure that the posted messages are acceptable based on guidelines.
What is the difference between asset allocation and diversification
Answers
Answer:
Asset allocation refers to the percentage of stocks, bonds, and cash in your portfolio. In contrast, diversification describes the spreading of your assets across the various asset classes within each of those three allocation buckets to further reduce risk.
Explanation:
Which of the following is the primary mechanism for representing the content of a Web page?A. HTMLB. tagC. attributeD. cookieE. hypertext
Answers
The primary mechanism for representing the content of a web page is HTML, which stands for Hypertext Markup Language. The correct option is (a) HTML.
The primary mechanism for representing the content of a web page is HTML, which stands for Hypertext Markup Language. HTML is used to structure the content of a web page, including text, images, and other media, and to specify how that content should be displayed in a web browser. HTML uses tags and attributes to define the structure and appearance of content on a web page. Tags are used to define elements such as headings, paragraphs, and lists, while attributes provide additional information about those elements, such as the color or size of text. Hypertext is another important aspect of web pages, allowing users to navigate between pages and access different types of content. Overall, HTML is the foundation of modern web development and is essential for creating functional, well-designed web pages.
To know more about web page visit: https://brainly.com/question/30856617
#SPJ11
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
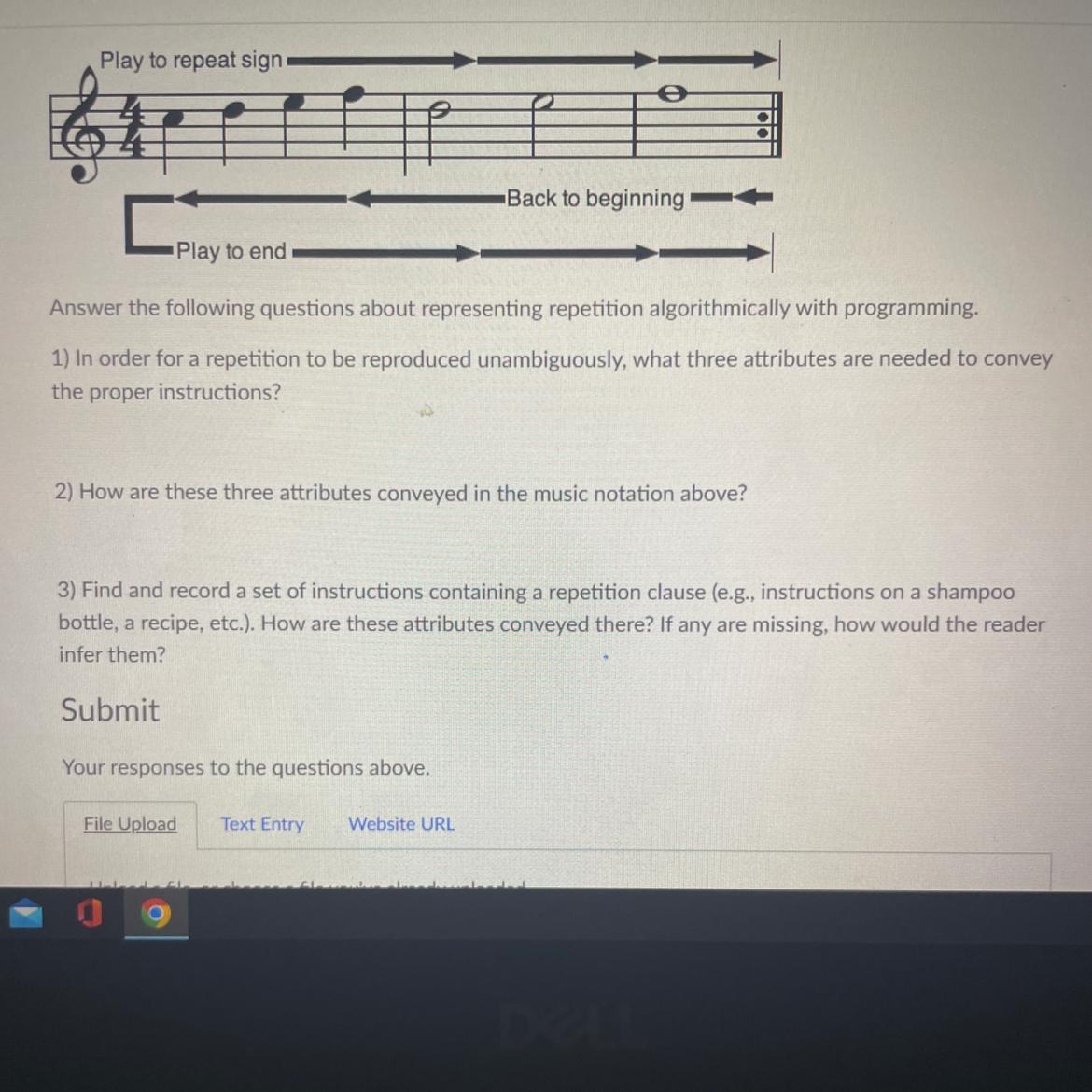
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
help me with this easy question that I can't do :)

Answers
Answer:
BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB
Answer: C. Trim unnecessary sound.
(I think this is right).
Explanation: Playback Controls is a floating window that give you a console for controlling the playback of your score. By clicking the expand arrow, Playback Controls expands to display a number of playback options, such as the tempo, range of measures to be played, overall volume level, and so on.
The execution of a machine code program on a von Neumann architecture computer occurs in a process called the ___ cycle.
Answers
The execution of a machine code program on a von Neumann architecture computer occurs in a process called the instruction cycle.
In the von Neumann model, machine code instructions are executed one at a time, and the instruction cycle is the sequence of events that occurs during the execution of each instruction.The instruction cycle includes a fetch cycle, decode cycle, and execute cycle. During the fetch cycle, the processor retrieves the next instruction from memory and loads it into the instruction register. During the decode cycle, the processor decodes the instruction to determine what operation it represents and which operands it should use.
During the execute cycle, the processor performs the operation specified by the instruction using the operands that were determined during the decode cycle.The machine code is a type of low-level programming language that consists of instructions written in binary code that a computer can understand. This code is written in a binary format, which is a series of 1s and 0s that represent specific instructions that a computer can execute. Machine code instructions are specific to a particular processor architecture and are executed directly by the processor without the need for any translation.
The von Neumann architecture is a type of computer architecture that is characterized by having a single memory space for both data and instructions. It is named after the mathematician and computer scientist John von Neumann, who first proposed this design. In the von Neumann architecture, the processor fetches instructions from memory and executes them one at a time. The von Neumann architecture is used in most modern computers because of its simplicity and flexibility.
To learn more about machine code:
https://brainly.com/question/17041216
#SPJ11
a router has separate forwarding and routing tables. if the forwarding table of a router is corrupted by an attacker, will routing still function properly? why?
Answers
If the forwarding table of a router is corrupted by an attacker, the routing function of the router may still function properly, but the router may not be able to forward packets correctly to their destination.
The forwarding table is a critical component of a router's operation. It maps destination addresses to outgoing interfaces, and it is used by the router to forward packets through the network. If the forwarding table is corrupted or inaccurate, the router may not be able to forward packets correctly, and some packets may be dropped or misrouted.
However, the routing function of the router may still function properly, even if the forwarding table is corrupted. The routing table is used by the router to determine the best path for packets to take through the network, based on the network topology and the routing protocol in use.
The routing table is not used directly for packet forwarding, but rather it is used to populate the forwarding table with correct information.
Learn more about router here:
https://brainly.com/question/24812743
#SPJ11
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
Under which license is open-source software available?
A non-perpetual license
B. perpetual license
Ос.
GNU General Public License
D.
site license
O E
license with maintenance
Answers
Answer:
GNU General Public License
Explanation:
The GNU's General Public License is the most popular open-source license around. Richard Stallman created the GPL to protect the GNU software from becoming proprietary, and it is a specific implementation of his "copyleft" concept.
There are eight floating-point data registers in the FPU, namely ST(0), ST(1), ST(2), ST(3), ST(4), ST(5), ST(6), and ST(7). The size of each floating point registers in bits is?A. 64 BitsB. 16 BitsC. 80 BitsD. 32 Bits
Answers
The correct response is C. 80 Bits. The size of each floating point registers in bits is 80 Bits..
Having a decimal point, a floating point number can be positive or negative. For instance, the floating point numbers 5.5, 0.25, and -103.342 all fall into this category, although 91 and 0 do not. Due to the decimal point's flexibility, floating point numbers can have any place for the decimal point. With a predetermined number of digits after, and occasionally before, the decimal point, this method of representing numbers is known as "fixed point." The decimal point can "float" in relation to the significant digits of a number when it is represented using floating-point math. According to the definition of floating point, a number's radix point can "float" anywhere between its significant digits or to the left or right of them.
Learn more about floating point here
https://brainly.com/question/15025184
#SPJ4
5.18 lab: adjust values in a list by normalizing when analyzing data sets, such as data for human heights or for human weights, a common step is to adjust the data. this adjustment can be done by normalizing to values between 0 and 1, or throwing away outliers. for this program, adjust the values by dividing all values by the largest value. the input begins with an integer indicating the number of floating-point values that follow. output each floating-point value with two digits after the decimal point, which can be achieved as follows: print(f'{your value:.2f}') ex: if the input is: 5 30.0 50.0 10.0 100.0 65.0 the output is: 0.30 0.50 0.10 1.00 0.65 the 5 indicates that there are five floating-point values in the list, namely 30.0, 50.0, 10.0, 100.0, and 65.0. 100.0 is the largest value in the list, so each value is divided by 100.0.
Answers
CODE :
n = int(input()) # get number of values in the list
values = list(map(float, input().split())) # get list of values
largest = max(values) # find the largest value
for val in values:
adjusted = val/largest # divide each value by the largest
print(f'{adjusted:.2f}') # print with 2 decimal places
How do float values work?
While 91 and 0 are not floating point numbers, 5.5, 0.25, and -103.342 are. The name "floating point numbers" refers to how the decimal point can "float" to any required location. Because of this, precision floating - point numbers are frequently referred to as "floats" in computer science. In computer science, integers, short, and long numbers are also frequent forms of numbers. These various types of integers are provided by certain programming languages but not by others. For instance, you must save the number 18 as an integer (int) and the value 50.3233 as a float in the language C. (float). However, JavaScript secretly treats all numbers, even numbers like 122, as floats.
To know more about Float values
https://brainly.com/question/13576263
#SPJ4
Adding applications that cannot tolerate jitter may require ________. Group of answer choices all of the above improved switch management improved security switch upgrades
Answers
Adding applications that cannot tolerate jitter may require all of the above.So correct answer is A
To understand the answer, let's first understand what Jitter is:Jitter is the variation in the delay between packets that are supposed to be sent between two endpoints. It happens because packets don't always travel through the same route to reach the destination. As a result, Jitter has a severe impact on the quality of communication, particularly in Voice over IP (VoIP) applications and other latency-sensitive applications. This is why adding applications that cannot tolerate Jitter may require all of the above.Improved switch management: If a network's switches are poorly managed, it may result in Jitter, particularly when bandwidth-hogging applications have to compete with low-priority traffic.
Improved security: Cyber threats, such as malware, ransomware, and distributed denial-of-service attacks, can cause Jitter in a network. As a result, having a robust security protocol can help minimize the likelihood of such events occurring.Switch upgrades: Switches must have the ability to minimize the effects of Jitter on latency-sensitive applications. As a result, if the switches are unable to meet the requirements of the applications, an upgrade may be required.
To know more about applications visit:
brainly.com/question/30900385
#SPJ11
independence day in school long passage plss
Answers
Answer:
Independence Day Celebration in My School
Fifteen August, is a red letter day in the history of India. On this day in 1947, our country become free form the long imprisonment of the British rule. Since 1947, fifteenth August is celebrated every year with great joy and pride. It reminds us for the great struggle of our freedom from the British rule. The great sacrifice for our freedom fighters is remembered, which serves as a beacon light for the development of this great country. The main function is held at Red Fort in Delhi where the Prime Minister unfurls the National flag. It is an occasion of celebration for every Indian and the whole nation celebrate a holiday from all work and take a pledge to work whole heatedly for the development of this country and preservation of Independence. All those who have stood out exclusively in their respective field of work are honored in public meetings. The whole nation pays homage to the security forces who have laid down their lives for the honor and security of the country.
We also celebrated the Independence day in our school compound, with great pump and show. The school building and the ground were cleaned and decorated for the occasion. A flag pole was put up at the top of the school building. The seating arrangement was made on the platform. Markings were made on the ground with white lines. The flower pots were kept all along the path.
There was great enthusiasm among students. The school band of students took its position half an hour before the actual function was to began. The members of the band were wearing a beautiful uniform. They began to play sweet tunes. The students had taken their places well before the time. They were all in school uniform, the white paint and white shirt.
The function began exactly at 8 a.m. all who were present stood in attention. The principal unfurled the flag. The petals of rose fell on us. Five boys sang a song in honor of the national flag. It was “Vijayee Vishwa Trianga Payara”. Them by the school band. The principal look the salute. He made an impressive speech and invited the Education Minster to impressive speech and invited the Education Minster to address us. In his address he asked us to take pledge to safeguard the freedom of nation. He also reminded us of great sons of India, Mahatma Gandhi, Pt. Nehru, Subhash Chandra Bose, Lala Lajpat Roy and Chander Shekar Azad and their sacrifices to the nation. After that different groups of students presented a programme of mass drill and pyramid formation. Ever one liked the programme.
In the end, all stood in attention. All the students, teachers and guardians sang the National Anthem in chorus. With this the function was over. Today the memories of this function are as alive to me, as it was on that day.