What advancements in technology enabled europeans to navigate the open ocean?.
Answers
The open ocean has always been a challenging and intimidating terrain for sailors due to its vastness and unpredictability. However, over the centuries, European sailors developed various technological advancements that helped them navigate the open ocean with greater ease and efficiency.
The astrolabe is an ancient astronomical device that measures the altitude of celestial objects, such as the sun and stars, above the horizon. With the astrolabe, European sailors could determine their position and the direction they needed to travel accurately.
In conclusion, the advancements in technology mentioned above were crucial to the exploration and expansion of European empires across the open ocean. With these innovations, European sailors were better equipped to navigate unknown waters and establish trade routes with other countries, which ultimately led to the colonization and exploitation of many parts of the world.
To know more about ocean visit:
https://brainly.com/question/11803537
#SPJ11
Related Questions
The process of converting software to operate in a second language is called software _______.
Answers
Answer:
software localization
Explanation:
As international systems penetrate deeper into management and clerical groups, a common language is formed
So I got the MSI GE76 Raider and I dont know if I should get a new better gaming laptop or not, is the GE76 good for gaming?
Answers
Answer:
yes it is
Explanation:
The MSI GE76 Raider is one of the best gaming laptops for those looking for a desktop replacement. It even brings excess amounts of RGB lighting courtesy of a full light bar under the wrist rest. Of course, that all comes at a cost.
What is the speedup when 10% of the code is not parallelized and the rest of the code is perfectly parallelized and executed on 9 cores?
Answers
Speedup is approximately 8.33 when 10% of the code is not parallelized and the remaining 90% is perfectly parallelized and executed on 9 cores.
Speedup is calculated as the time taken by the sequential program divided by the time taken by the parallel program. In this scenario, assuming the non-parallelizable portion takes 100 units of time, the parallelizable portion takes 10 units of time on a single core. When executed on 9 cores, the parallelizable portion takes only 1.11 units of time, resulting in a total time of 101.11 units. Speedup is approximately 8.33 when 10% of the code is not parallelized and the remaining 90% is perfectly parallelized and executed on 9 cores. Therefore, the speedup is 100/101.11, which is approximately 8.33.
learn more about code here:
https://brainly.com/question/17293834
#SPJ11
Son aplicaciones desarrolladas específicamente para realizar actividades otareas que se llevan a cabo en oficinas o en educación.
Answers
Las herramientas ofimáticas son aplicaciones desarrolladas específicamente para realizar actividades o tareas que se llevan a cabo en oficinas o en educación.
Estas son las diversas computadoras y software que se utilizan para crear, recopilar, almacenar, manipular y transmitir digitalmente la información necesaria para realizar tareas básicas en los ámbitos educativos o comerciales.
Al automatizar las operaciones de la oficina, es posible lograr una mayor cantidad de tareas más rápido; además elimina la necesidad de una gran cantidad de empleados; y permite que se requiera menos espacio de almacenamiento de datos.
Aprende más en https://brainly.com/question/21750706
which field data type would you use if youd like to store videos in that field?
A. text
B. memo
C.boolean
D. binary object
E. null
Answers
Answer:
D - Bianary Object
Explanation:
A binary large object is a collection of binary data stored as a single entity. Blobs are typically images, audio or other multimedia objects, though sometimes binary executable code is stored as a blob. They can exist as persistent values inside some databases or version control system, or exist at runtime as program variables in some programming. - Wikipedia
Pre-Test
Active
2
3
6
7
8
9
In order for a fictionalized story to be based on real events, the author should include
O characters with strong feelings
O historical matenal
O a narrator
O dialogue
Answers
Some of the options in this question are not correct; here is the correct and complete question:
In order for a fictionalized story to be based on real events, the author should include
A. Characters with strong feelings
B. Historical material
C. A narrator
D. Dialogue
The correct answer is B. Historical material
Explanation:
Stories, novels, and poems are said to be based on real events if these include or are inspired by real people, settings, or historical events. This includes using any historical material and adapting it to create a story. For example, the play "The Tragedy of Julius Caesar" written by Shakespeare is a play based on real events as it includes real characters such as Julius Caesar and some of the events in it are based on historical events.
According to this, the element that is necessary to make a story to be based on real events is historical material. Also, others such as a narrator, dialogue, or characters with strong feelings can be found in most stories including those that are completely fictionalized.
Sam wanted to send a document quickly to an individual 300 miles away. Sam used a
motherboard
fax machine
scanner
O hard drive
Answers
Answer:
Fax Machine its faster and digital
Please please please help I beg I'll give brainiest. :(
A digital egg timer uses an input, process and output. (a) Suggest an appropriate input component. (b) Suggest an appropriate output component (c) Circle the most appropriate device below to be used for the timing process. Monostable or Astable
Answers
Answer:
A) toggle switch B) Push to Make switch C) Monostable
Explanation:
toggle because it needs to go off when the timer ends and not when u press a button
Push to make because you turn the timer off manually
Monostable because it needs to go off once not repeatedly
5. Draw a block diagram showing the following components of a computer: (Double click on the drawing to open the draw tool) Insert the following: Input, Output, Storage, main memory and the CPU. INPUT [5] [Total 15 marks]
Answers
A computer is made up of diverse elements, such as a CPU, input devices, output devices, main memory, and storage devices.
What is the function of an input device?Input devices are utilized to furnish the computer with data and commands. Input devices that are commonly used include a keyboard, mouse, scanner, and microphone.
Computer-generated output is presented using output devices. Output devices comprise of a display screen, printing machine, and audio emitting apparatus.
Data and programs can be kept in storage devices. Various types of storage devices are available, such as hard disk drives, solid-state drives, and flash drives.
Main memory, or RAM, is a form of ephemeral storage employed to hold data and commands that are currently being handled by the CPU.
The central processing unit, often abbreviated as CPU, serves as the computer's primary "thinking" component. It is responsible for carrying out the necessary computations and commands while also regulating the actions of the rest of the computer's hardware.
When combined, these elements create the fundamental structure of a computer setup.
Read more about computer here:
https://brainly.com/question/24540334
#SPJ1

The HIPAA data integrity standard requires that organizations do which of the following?
a. Keep documented logs of system access and access attempts
b. Assign role-based access privileges
c. Establish workstation security
d. Conduct workforce training for correct data input
Answers
The HIPAA data integrity standard requires that organizations do all of the following in order to ensure the integrity and confidentiality of patient information.
This includes keeping documented logs of system access and access attempts, assigning role-based access privileges to employees and third-party users, establishing workstation security measures, and conducting workforce training for correct data input. By implementing these measures, healthcare organizations can ensure that only authorized individuals have access to patient information and that all data is entered accurately and securely. Failure to comply with these requirements can result in significant penalties and legal consequences, making it essential for organizations to take data integrity seriously.
learn more about HIPAA here:
https://brainly.com/question/29870974
#SPJ11
Which of the following storage methods is used for storing long-term copies of organizational data? Select one: a. backup. b. archival. c. translational.
Answers
Archival, storage methods is used for storing long-term copies of organizational data.
What is Metadata ?Metadata condensed information about data in order to facilitate dealing with a particular instance of data.
Metadata is typically present in spreadsheets, websites, movies, and pictures.
The availability of metadata facilitates data tracking and dealing with such data.
The time and date of creation, file size, data quality, and date produced are all examples of basic document metadata.
Metadata management and storage usually include the usage of databases.
Hence, Archival, storage methods is used for storing long-term copies of organizational data.
learn more about Metadata click here:
brainly.com/question/14960489
#SPJ4
Explain how Steve Jobs created and introduced the iPhone and iPad.
Answers
Answer:Today, we're introducing three revolutionary products. The first one is a widescreen iPod with touch controls. The second is a revolutionary mobile phone. And the third is a breakthrough Internet communications device. So, three things: a widescreen iPod with touch controls, a revolutionary mobile phone, and a breakthrough Internet communications device. An iPod, a phone, and an Internet communicator. An iPod, a phone...are you getting it? These are not three separate devices. This is one device. And we are calling it iPhone. Today, Apple is going to reinvent the phone.
Late last year, former Apple engineer Andy Grignon, who was in charge of the radios on the original iPhone, gave behind-the-scenes look at how Apple patched together demos for the introduction, with Steve Jobs showing off developmental devices full of buggy software and hardware issues. The iPhone team knew that everything had to go just right for the live iPhone demos to succeed, and they did, turning the smartphone industry on its head even as Apple continue to scramble to finish work on the iPhone.
Apple had actually been interested first in developing a tablet known as "Safari Pad", but as noted by a number of sources including Steve Jobs himself, the company shifted gears once it became clear how revolutionary the multi-touch interface developed for the tablet could be for a smartphone. Apple's tablet wouldn't surface until the launch of the iPad in 2010, three years after the introduction of the iPhone.
Seven years after the famous Macworld 2007 keynote, the iPhone has seen significant enhancements in every area, but the original iPhone remains recognizable as Apple has maintained the overall look of a sleek design with a larger touchscreen and a single round home button on the face of the device.
Explanation:
Brenda typed a few lines on a word processor. She then pressed F7 key to proofread her file. What type of key did Brenda press?
OA. function
OB. alphabetic
OC. numeric
OD. punctuation
O E. control
Pls help
Answers
Answer:
Function key
Explanation:
Given
F7 Key
Required
What does it stand for?
On a computer keyboard, the F7 key is one of the function keys.
There are 12 function keys labelled F1 to F12, each of which have designated functions.
So, from the list of given options, option A answers the question.
Analyzing other options:
Alphabetic implies A - Z in upper and lower case
Numeric implies digits 0 to 9
Punctuation implies punctuation marks such as . , ; : etc.
Control implies the ctrl key
Answer:
aa
Explanation:
What is computing device
Answers
Please do mark me as Brainiest. I would be so happy!!!
Answer:
Any electronic equipment controlled by a CPU, including desktop and laptop computers, smartphones and tablets. It usually refers to a general-purpose device that can accept software for many purposes in contrast with a dedicated unit of equipment such as a network switch or router.
Have a great day.
Answer:
Explanation:
ASAP
There are two competing scientific theories that try to explain the illusion of animation. Which of these answers is NOT one of the competing theories?
Persistence of Vision
Image-permanence
Phi Phenomenon
The first who answers correct will get brainlest and those that are incorrected will be marked with a red flag.
Answers
which line of code will allow you to only load the localtime() method into active memory

Answers
Answer:
from time import localtime
Explanation:
have a lovely day :)
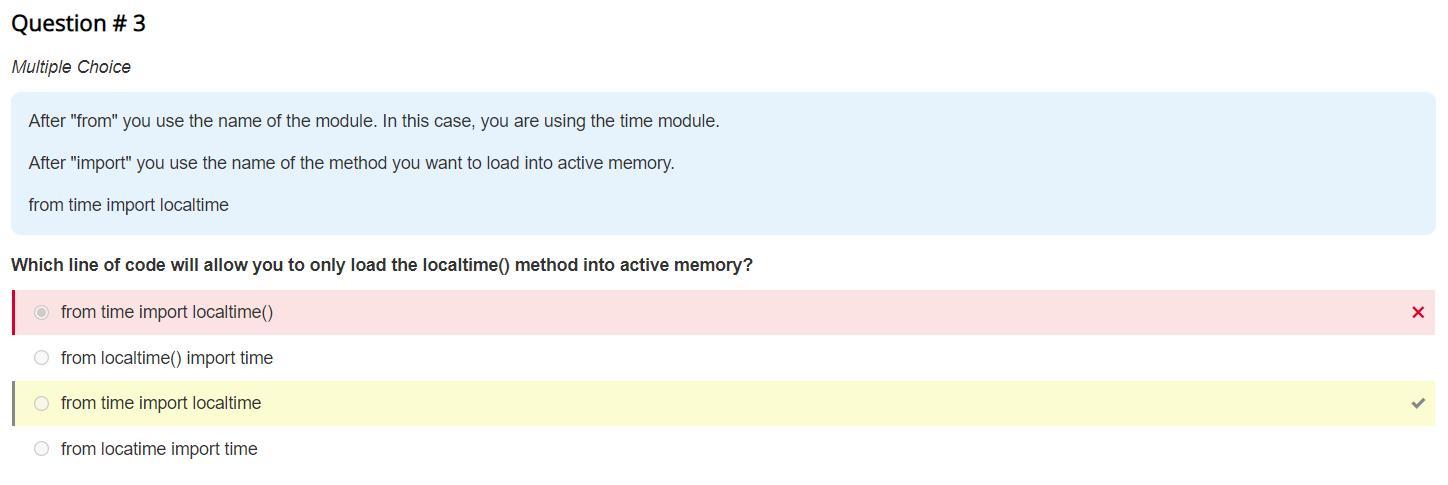
The line of code that will allow you to only load the localtime method into active memory is time.
The localtime function is simply known to be time in seconds as long as Epoch is targeted by timer into a broken-down time.
It is mostly written in local time. The function is known to be of timezone and any seasonal time adjustments. Local timezone information is used as though localtime() calls tzset().LocalTime cannot have a muted date-time object that shows a time, often viewed as hour-minute-second. Time is shown in nanosecond precision.
Learn more from
https://brainly.com/question/19639119
Which of the following might increase economic efficiency in a fast-food restaurant?
long lines for customers
flexible hours for workers
not enough workers to take care of customers
all of the above
Answers
Answer:
I think B.
Explanation:
It may be wrong but, B makes the most since. I don't know how, sorry if I'm wrong!
Answer:
look
Explanation:
The labor market continues to recover, but a stubbornly high rate of underemployment persists as more than five million Americans are working part-time for economic reasons (U.S. BLS 2015a; 2015b). Not only are many of this type of underemployed worker, by definition, scheduled for fewer hours, days, or weeks than they prefer to be working, the daily timing of their work schedules can often be irregular or unpredictable. This both constrains consumer spending and complicates the daily work lives of such workers, particularly those navigating through nonwork responsibilities such as caregiving. This variability of work hours contributes to income instability and thus, adversely affects not only household consumption but general macroeconomic performance.
The plight of employees with unstable work schedules is demonstrated here with new findings, using General Social Survey (GSS) data. These findings (as well as key findings from other research) are highlighted below.
a program which randomly picks 5 cards from a deck. explain what functions of the deck are being utilized.
Answers
A program which randomly picks 5 cards from a deck. Explain what functions of the deck are being utilized.:A deck in programming is essentially an array of cards or an object. The deck can contain cards, as well as various functions that manipulate cards within the deck.
A program that selects five random cards from a deck is an excellent example of utilizing the function of a deck in a program.In order to pick five random cards from a deck in programming, the following functions of a deck are being utilized:1. Shuffling Function:In programming, shuffling is one of the most frequently used deck functions. The shuffle function is utilized to randomly rearrange the card order in the deck. It is critical to ensure that the deck is randomized before it is used to choose any cards, otherwise the result will not be truly random.2. Select Function:The select function is another vital function of a deck. It is responsible for choosing a specific number of cards from the deck. In this case, the select function is used to select five cards randomly from the deck.3. Remove Function:The remove function, or any other function that extracts cards from a deck, is used after the select function has chosen the desired number of cards. The remove function is utilized to remove the selected cards from the deck so that they do not appear again during the selection process.:
In the above problem, a program selects five random cards from a deck. A deck is an array of cards or an object in programming. It can contain cards as well as various functions that manipulate cards within the deck.In order to pick five random cards from a deck in programming, we use the following functions of a deck:1. Shuffling FunctionIn programming, shuffling is one of the most frequently used deck functions. The shuffle function is utilized to randomly rearrange the card order in the deck. It is critical to ensure that the deck is randomized before it is used to choose any cards, otherwise the result will not be truly random.In this program, we must use the shuffle function before selecting any cards from the deck. This will ensure that the cards are arranged randomly, and the five cards chosen will be truly random.2. Select FunctionThe select function is another vital function of a deck. It is responsible for choosing a specific number of cards from the deck. In this case, the select function is used to select five cards randomly from the deck.Once the shuffle function has randomized the deck, we can use the select function to pick five random cards from the deck.3. Remove FunctionThe remove function, or any other function that extracts cards from a deck, is used after the select function has chosen the desired number of cards.
To know more about program visit :
https://brainly.com/question/30613605
#SPJ11
What is output if the user types in 8? Click all that apply.
Answers
Answer:
can u show a picture??? or something
you lose your job and, as a result, you buy fewer itunes music downloads. this shows that you consider itunes music downloads to be
Answers
When the consumer's income improves, or in this case, drops, the demand for an inferior good type decreases. Your income declines if you lose your work.
What happens to a subpar product as customer spending rises?In economics, when income rises or the economy grows, the demand for subpar products declines. Customers will be more likely to spend money on more expensive alternatives when this occurs.
When is a good a lesser good?When consumer incomes increase, demand for an inferior good declines. An inferior good is one that is less in demand when wages rise or fall, even though it is not worse in quality.
To know more about consumer's visit:-
https://brainly.com/question/14286560
#SPJ1
Read the integer numbers in the text file "1000 Random Number from 0 to 100.txt" into a list
PLEASE HELP THANK U!!
Answers
Answer:
random_number_file = open("1000 Random Number from 0 to 100.txt", 'r')
random_number_list = random_number_file.readlines()
print('random_number_list)
Explanation:
The name of the file containing the random integer text is ; "1000 Random Number from 0 to 100.txt"
The random_number_file variable stores the opened file ("1000 Random Number from 0 to 100.txt") using the open keyword and reads it ('r')
This file stored in the random_number_file variable is the read into a list by using the readlines() method on the random_number_file
What is
social-media ?
Answers
Social media is computer-based technology that facilitates the sharing of ideas, thoughts, and information through the building of virtual networks and communities. By design, social media is internet-based and gives users quick electronic communication of content.
Answer:
You asked a good question.
For example: Twitter, Face book, Instagram... Are called social media in which they are apps/websites that connect you to the community and let you create and share content with other people quickly and efficiently.Many people define social media as apps on their smartphone, tablet, or computer.
\(hope \: this \: helps\)
name two components required for wireless networking
(answer fastly)
Answers
Explanation:
User Devices. Users of wireless LANs operate a multitude of devices, such as PCs, laptops, and PDAs. ...
Radio NICs. A major part of a wireless LAN includes a radio NIC that operates within the computer device and provides wireless connectivity.
or routers, repeaters, and access points
who provides cloud computing services for sale to third parties? cloud regulator cloud customer cloud service provider cloud service partner
Answers
The entity that provides cloud computing services for sale to third parties is called a cloud service provider. These providers offer a wide range of services, such as infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) to customers, who can then use these services to store, process, and manage their data and applications.
1)Cloud service providers often work with cloud service partners to enhance their services and expand their reach. These partners can be technology vendors, system integrators, or consultants, who provide complementary services such as migration, integration, and customization to customers.
2)Cloud regulators may play a role in ensuring that cloud service providers comply with industry standards and regulations, but they do not provide cloud computing services for sale themselves.
3)Ultimately, it is the cloud customer who benefits from the services provided by cloud service providers. They can choose from a variety of providers and services based on their specific needs and requirements, and pay for these services on a usage-based or subscription-based model. This allows them to access the latest technology and capabilities without the need for expensive infrastructure investments.
For such more questions on cloud computing services
https://brainly.com/question/19057393
#SPJ11
a technician is configuring a computer lab for the students at dion training. the computers need to be able to communicate with each other on the internal network, but students using computers should not be able to access the internet. the current network architecture is segmented using a triple-homed firewall to create the following zones: zone interface, ip address --------------------------------------- public, eth0, 66.13.24.16/30 instructors, eth1, 172.16.1.1/24 students, eth2, 192.168.1.1/24 what rule on the firewall should the technician configure to prevent students from accessing the internet?
Answers
The technician should configure a rule on the firewall to block all outgoing traffic from the students' zone (eth2) to the public zone (eth0). This can be achieved by creating an outbound firewall rule on the eth2 interface that denies all traffic to the IP range of the internet (e.g. 0.0.0.0/0). This will ensure that the computers in the lab can communicate with each other on the internal network, but students will not be able to access the internet.
This will prevent any packets originating from the student computers in the "192.168.1.0/24" subnet from reaching the internet, effectively preventing them from accessing the internet while allowing communication among computers within the internal network. Additionally, the technician should ensure that there are no other rules that contradict or override this outbound rule to ensure proper network segmentation and internet access restriction for the students.
learn more about Firewall rule here:
https://brainly.com/question/29590548
#SPJ11
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
Which type of operating system is permanently programmed into a hardware device?
A. Embedded OS
B. Firmware
C. Mobile OS
D. Hypervisor
Answers
Answer:
B.FIRMWARE
Explanation:
An operating system that is permanently etched into a hardware device (such as a keyboard or a video card).
The type of operating system is permanently programmed into a hardware device is firmware. The correct option is B.
What is firmware?A platform's hardware components are configured and controlled by firmware, which is often computer code. As a result, firmware typically executes as the first piece of code when a device is turned on, serving as the cornerstone upon which system trust is based.
Firmware is a class of software that is permanently included in a device's read-only memory. It offers instructions on how to operate the device and reduces hardware-level security risks. Essentially, firmware refers to software that is integrated into a piece of hardware.
It is referred to as embedded software at times. A microcontroller, a component of the microprocessor that instructs the microprocessor on what to do, serves as an illustration.
Therefore, the correct option is B. Firmware.
To learn more about firmware, refer to the link:
https://brainly.com/question/28945238
#SPJ2
To determine why a computer program started to function differently, Mel should most likely use data to......
A)confirm her belief that something is wrong.
B) convince the software company of the issue.
C) understand why the issue is occurring.
D)evaluate the effectiveness of other software
Answer "C", understand why the issue is occurring.
Putting this out there for others that need it in the future.
Answers
The answer would be (B) convince the software company of the issue.
Answer:
c
Explanation:
most computers have temporary holding areas called __________.
Answers
Answer:
Random Access Memory (RAM)
For the main memory address 0:0:0, briefly explain how a search is performed in two-way setassociative mapping. Assume that the main memory size is 4 GB, the cache memory is 8 KB and the size of cache block is 32 bytes
Answers
A two-way set-associative mapping divides the cache into sets containing two blocks, and uses index bits to determine which set a memory address belongs to. The cache controller then checks both blocks in that set for a match, resulting in a cache hit or miss.
In a two-way set-associative mapping, the cache is divided into sets, and each set contains two cache blocks. The index bits of the main memory address are used to determine which set the address belongs to. In this case, since the cache size is 8 KB (or 8192 bytes), and the cache block size is 32 bytes, there are 256 cache blocks in total (8192/32).
To search for a main memory address in the cache, the cache controller first looks up the index bits of the address to determine which set the address belongs to. Then, it checks both cache blocks in that set for a match. If the address is found in one of the cache blocks, it is considered a cache hit, and the data is retrieved from the cache. If the address is not found in either cache block, it is considered a cache miss, and the data must be retrieved from main memory and loaded into one of the cache blocks in the corresponding set.
For the main memory address 0:0:0, the index bits would be 0:0, since the cache is divided into 256 sets (2^8 = 256). Therefore, the cache controller would first look in set 0, and check both cache blocks for a match. If the address is not found, it would be considered a cache miss, and the data would need to be retrieved from main memory and loaded into one of the cache blocks in set 0.
Know more about the main memory click here:
https://brainly.com/question/30435272
#SPJ11