which of these is an accurate description of arc welding and cutting?
Answers
Arc welding and cutting are processes that use an electric arc to join or cut meta, ln welding the arc melts the metal at the joint, which then cools and solidifies to form a strong bond.
In cutting, the arc melts the metal at the desired point, and the molten metal is blown away by a jet of gas to create a cut. Both processes require a power source, electrodes, and safety equipment such as helmets and gloves. Cutting is a process that is used to remove material from a workpiece, typically by using a tool or machine that generates heat or force to cut through the material.
One method of cutting is arc cutting, which uses an electric arc to melt the metal at the desired point, and then blows the molten metal away using a jet of gas to create a cut.
Learn more about Arc welding: https://brainly.com/question/14618899
#SPJ11
Related Questions
what management console will specifically allow you to configure your hyper-v permissions to accomplish this task?
Answers
To configure your Hyper-V permissions to accomplish a specific task, you will require the Hyper-V Manager console.
The Hyper-V Manager is a Microsoft Windows administrative tool that enables users to configure and manage Hyper-V virtual machines (VMs).
Microsoft's Hyper-V is a virtualization platform that runs on the Microsoft Windows operating system. Hyper-V allows users to create and run virtual machines on a single physical computer, providing multiple computing environments that can coexist on a single server.
Hyper-V supports a variety of operating systems, including Windows, Linux, and others. It is a hardware virtualization solution that enables the user to run multiple VMs on a single physical server, each with its own operating system, virtual hardware, and applications.
In conclusion, the Hyper-V Manager is the specific management console that will allow you to configure your Hyper-V permissions to accomplish a specific task.
Learn more about Hyper-V Manager console:https://brainly.com/question/28322407
#SPJ11
Explain how Steve Jobs created and introduced the iPhone and iPad.
Answers
Answer:Today, we're introducing three revolutionary products. The first one is a widescreen iPod with touch controls. The second is a revolutionary mobile phone. And the third is a breakthrough Internet communications device. So, three things: a widescreen iPod with touch controls, a revolutionary mobile phone, and a breakthrough Internet communications device. An iPod, a phone, and an Internet communicator. An iPod, a phone...are you getting it? These are not three separate devices. This is one device. And we are calling it iPhone. Today, Apple is going to reinvent the phone.
Late last year, former Apple engineer Andy Grignon, who was in charge of the radios on the original iPhone, gave behind-the-scenes look at how Apple patched together demos for the introduction, with Steve Jobs showing off developmental devices full of buggy software and hardware issues. The iPhone team knew that everything had to go just right for the live iPhone demos to succeed, and they did, turning the smartphone industry on its head even as Apple continue to scramble to finish work on the iPhone.
Apple had actually been interested first in developing a tablet known as "Safari Pad", but as noted by a number of sources including Steve Jobs himself, the company shifted gears once it became clear how revolutionary the multi-touch interface developed for the tablet could be for a smartphone. Apple's tablet wouldn't surface until the launch of the iPad in 2010, three years after the introduction of the iPhone.
Seven years after the famous Macworld 2007 keynote, the iPhone has seen significant enhancements in every area, but the original iPhone remains recognizable as Apple has maintained the overall look of a sleek design with a larger touchscreen and a single round home button on the face of the device.
Explanation:
Shreya has combined all the cells in a single leftmost column in a table. Instead of identifying the category multiple times, she would like to combine these cells and then structure the word "Appliances” vertically in the cell.
Where will Shreya find these options?
1. Insert tab, Tables group
2. Design tab, Merge group
3. Table Tools Design tab, Merge group
4. Table Tools Design tab, Merge group, Alignment group
Answers
Answer:
B. Design tab, Merge group
Explanation:
Research the history of Internet in computers
Answers
Answer:
This allowed different kinds of computers on different networks to "talk" to each other. ARPANET and the Defense Data Network officially changed to the TCP/IP standard on January 1, 1983, hence the birth of the Internet. All networks could now be connected by a universal language.
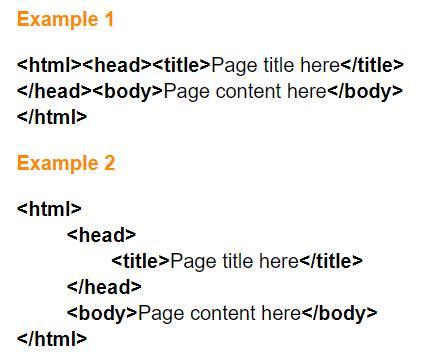
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
How do graphic designers showcase their work?
Graphic designers create(Blank)
to showcase their work.
THIS IS A BIG TEST IM BEHIND AND CANNOT FAIL PLZ
Answers
Answer:
Platforms!
Explanation:
Answer:
portfolios
Explanation:
A portfolio is a collection of work done by a graphic designer. Graphic designers use them to display their work to their clients.
Reply to the comment with the following replace variation with variety
Answers
The term "variation" and "variety" may sound alike and similar but they have a different definition. Variation refers to the differences between individuals of the same species, while variety means the presence of many different types of something.
Hence, to replace "variation" with "variety," you will need to provide an explanation about different types of something.In a context where someone made a comment with the word "variation," you can reply using a phrase that uses the word "variety." For example, if the comment was, "I love the variation in colors in the sunset," you could reply, "I agree, the sunset's variety of colors is truly stunning.
It's amazing how different they can look each day. "When using the term "variety," it's essential to include a brief explanation to show the reader that you understand the definition of the word and how it relates to the context. Therefore, when using the phrase, you should aim for an explanation that is more than 100 words.
To know more about Variation visit:
https://brainly.com/question/11333978
#SPJ11
Is constructing a decision tree to visually represent the logic in a multi outcome if problem is often recommended?
Answers
Answer:
Yes, constructing a decision tree to visually represent the logic in a multi outcome if problem is often recommended.
một số được gọi là thác đổ nếu phần tử biểu diễn thập phân của nó nhiều hơn một chữ số đồng thời theo chiều từ trái qua phải chữ số đứng trước lớn hơn chữ số đứng sau
dữ liệu vào tệp THACDO.INP gồm nhiều dòng,mỗi dòng chứa số nguyên N
kết quả ra tệp THACDO.OUT gồm nhiều dòng thông báo,mỗi dòng ghi "CO" nếu N là thác đổ và ngược lại thông báo "KHONG" nếu N không phải
Answers
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
true or false: unlike starting a cable or satellite tv channel, starting an internet tv channel can be easy.
Answers
Internet TV channel is easy so it's true.
PLEASE HELP U GET A LOT OF POINTS AND MARKED BRAINLIEST
This is a java question.
How do you make a if statement in a while loop, so the if statements condition is that if the while loop is on the second run?
Answers
Answer:
Conditional statements with the proper comparison and boolean operators allow the creation of alternate execution paths in the code. Loops allow repeated execution of the same set of statements on all the objects within a sequence. Using an index based for loop is best suited for making changes to items within a list.
Explanation:
A train traveled at a constant speed for six hours and traveled a distance of 408 miles. What is the best estimate of the number of miles the train could travel in 2.5 hours? *
Answers
Answer:
this is math but htthe answer is 163.2 but you can just put 163
Expla
(Wattan Corporation) is an Internet service provider that charges customers a flat rate of $7. 99 for up to 10
hours of connection time. Additional hours or partial hours are charged at $1. 99 each.
Write a function charges that computes the total charge for a customer based on the number of hours of
connection time used in a month. The function should also calculate the average cost per hour of the time
used (rounded to the nearest 0. 01), so use two output parameters to send back these results.
You should write a second function
round_money that takes a real number as an input argument and returns as the function value the number
rounded to two decimal places. Write a main function that takes data from an input file usage. Txt and
produces an output file charges. Txt. The data file format is as follows:
Line 1: current month and year as two integers
Other lines: customer number (a five-digit number) and number of hours used
Here is a sample data file and the corresponding output file:
Data file usage. Txt
10 2009
15362 4. 2
42768 11. 1
11111 9. 9
Output file charges. Txt
Charges for 10/2009
15362 4. 2 7. 99 1. 90
42768 11. 1 10. 18 0. 92
11111 9. 9 7. 99 0. 81
Answers
The output file contains the charges for each customer, including the flat rate and any additional charges, as well as the average cost per hour.
What does the charges function do in this problem?To solve this problem, you need to write three functions: `charges`, `round_money`, and `main`. The `charges` function calculates the total charge for a customer and their average cost per hour, given the number of hours used. The `round_money` function rounds a number to two decimal places.
The `main` function reads the input file, calls `charges` for each customer, and writes the results to the output file. The input file contains the current month and year on the first line, followed by customer numbers and the number of hours used.
The output file contains the charges for each customer, including the flat rate and any additional charges, as well as the average cost per hour.
Learn more about Charges function
brainly.com/question/16529129
#SPJ11
mail cannot save information about your mailboxes because there isn’t enough space in your home folder.
Answers
Answer:
what is your question?
Explanation:
100 POINTS PLEASE HELP Ken Thompson and Dennis Ritchie co-created which operating system?
Answers
Answer:
UNIX operating system
Explanation:
Unix is a family of multitasking, multiuser computer operating systems that derive from the original AT&T Unix, development starting in the 1970s at the Bell Labs research center by Ken Thompson, Dennis Ritchie, and others.
Answer:
the UNIX
During the 1960s to 1970s, Bell Labs colleagues Ken Thompson and Dennis Ritchie developed UNIX, a multi-tasking, multi-user operating system alternative to the batch processing systems then dominating the computer industry.
Explanation:
Consider the following ip address: 172.17.8.10/22. which subnet mask is assigned to this address?
Answers
A subnet mask exists as a 32-bit number created by setting host bits to all 0s and setting network bits to all 1s.
What is IP address?An IP address, or Internet Protocol address, stands for a series of numbers that identifies any device on a network. Computers utilize IP addresses to communicate with each other both over the internet as well as on other networks.
A subnetwork or subnet exists as a logical subdivision of an IP network. The practice of separating a network into two or more networks exists called subnetting. Computers that belong to the same subnet stand addressed with an identical most-significant bit-group in their IP addresses.
A subnet mask exists as a 32-bit number created by setting host bits to all 0s and setting network bits to all 1s. In this way, the subnet mask divides the IP address into the network and host addresses. The “255” address exists always assigned to a broadcast address, and the “0” address is always designated to a network address.
To learn more about subnet mask refer to:
https://brainly.com/question/27960959
#SPJ4
How is data transmitted between computers?
Answers
Answer:
Data is transmitted from one computer to another through a process called serial transmittion
Serial data transmission sends data bits one after another over a single channel.
Hope this helps
the communication process begins when the sender . a. encodes an idea into a message b. has an idea c. determines the appropriate communication channel
Answers
The communication process begins when the sender has an a. encodes an idea.
The communication process involves several components, including the sender, the message, the channel, the receiver, and feedback. The sender is the person or entity that initiates the communication by having an idea or information to convey. Once the sender has an idea or message, they must encode it into a form that can be transmitted to the receiver, such as through spoken or written language, or through visual or audio media. While the sender may also determine the appropriate communication channel for the message, this typically comes after the idea or message has been formed and encoded.
Learn more about communication process: https://brainly.com/question/28319466
#SPJ11
suppose you are interested in detecting the number of hosts behind a nat. you observe that the ip layer stamps an identification number sequentially on each ip packet. the identification number of the first ip packet generated by a host is a large random number, and the identification numbers of the subsequent ip packets are sequentially assigned. assume all ip packets generated by hosts behind the nat are sent to the outside world.
Answers
Because all IP packets are broadcast to the outside world, we can employ a packet sniffer to capture all IP packets created by hosts behind a NAT.
We can arrange IP packets with successive IDs into a cluster because each host creates a sequence of IP packets with sequential numbers and a separate beginning ID. The cluster count signifies the number of hosts behind the NAT.
What is an IP Packet?A network packet is a structured unit of data transported by a packet-switched network in telecommunications and computer networking. A packet is made up of control information and user data, which is often referred to as the payload. Control data offers information for conveying the payload.
The Internet Protocol (IP) is a network layer protocol that deals with routing. It ensures that packets reach at their intended destination. The protocol that packets use can occasionally define them.
Learn more about IP Packet:
https://brainly.com/question/13322934
#SPJ1
Full Question:
Suppose you are interested in detecting the number of hosts behind a NAT. You observe that the IP layer stamps an identification number sequentially on each IP packet. The identification number of the first IP packet generated by a host is a random number, and the identification numbers of the subsequent IP packets are sequentially assigned. Assume all IP packets generated by hosts behind the NAT are sent to the outside world.
A) Based on this observation, and assuming you can sniff all packets sent by the NAT to the outside, can you outline a simple technique that detects the number of unique hosts behind a NAT?
What is the difference between cyberbullying and bullying.
Answers
Answer:
cyber bullying is more online other than normal bullying is face to face
Explanation:
Which of the following steps does a data scientist take before determining usable results?
Answers
Before determining usable results, a data scientist takes several steps to ensure the accuracy and validity of their findings. First, they define the problem and clearly articulate the hypothesis they are investigating. Next, they gather and clean the relevant data, ensuring that it is accurate and complete. This may involve removing duplicates, correcting errors, and filling in missing values.
Once the data is cleaned, the data scientist will then explore it using statistical analysis and visualization techniques. This allows them to identify patterns, trends, and relationships in the data and determine which variables are most relevant to the research question. They may also use machine learning algorithms to identify patterns that are not immediately apparent.
After analyzing the data, the data scientist will then develop and test models to determine which best predicts the outcome of interest. This involves selecting the appropriate model, tuning its parameters, and evaluating its performance using cross-validation or other techniques.
To know more about data scientist visit:-
https://brainly.com/question/24269857
#SPJ11
You have an unsorted array of 1,000,000
people.
You are using a Linear Search to look for
someone who is not in the array at all.
How many people does the computer look at
before it realizes this person is not in the array?
O a
b
Ос
Od
(a)exactly 1
(b)about 500,000
(c)all 1,000,000
(d) it will search forever
(d)It will search forever.
Answers
Deciding if a cyberattack is serious enough to warrant shutting down or disconnecting a critical system from the network is a difficult decision. What factors do you believe should be taken into account when making this decision and why are they important. Be detailed in your response.
Answers
Factors to consider for cyberattack : Impact assessment, attack progression, risk to safety/security, containment effectiveness, business impact, regulatory compliance. These factors are important to protect system integrity and prevent further damage.
When deciding whether to shut down or disconnect a critical system from the network due to a cyberattack, several factors should be considered:
Impact Assessment: Evaluate the potential consequences of the cyberattack on the critical system, including the extent of damage, loss of data, disruption of services, and potential harm to individuals or infrastructure.Attack Vector and Progression: Determine the attack vector used and assess how the attack is progressing. If the attack is spreading rapidly or exploiting critical vulnerabilities, immediate action may be necessary.Risk to Safety and Security: Assess the risks to the safety of personnel, public safety, national security, or the physical infrastructure associated with the critical system. If there is a significant risk, disconnecting or shutting down the system may be necessary.Containment and Mitigation Measures: Evaluate the effectiveness of current containment and mitigation measures. If the attack is evading or bypassing existing defenses, shutting down or disconnecting the system may be required to prevent further damage.Business Impact: Consider the potential financial and operational impact of shutting down or disconnecting the critical system. Balancing the potential consequences of the cyberattack with the impact of disruption is crucial.Regulatory and Legal Obligations: Consider any legal or regulatory requirements regarding cyber incident response and reporting. Compliance with applicable laws and regulations is essential in making the decision.These factors help organizations make informed decisions based on the potential risks, impact, and overall security posture, ensuring the protection of critical systems and minimizing the impact of cyberattacks.
For more such question on Cyberattack
https://brainly.com/question/27665132
#SPJ8
Question 15(Multiple Choice Worth 6 points)
(03.02 MC)
Which of the actions below becomes part of your digital identity?
O Meeting a friend at a juice shop
Attending your school's prom
Borrowing a neighbor's blender
Responding to an email
Answers
Answer:
Responding to an email
Explanation:
I did the assignment. The other ones you do not use any technology, while you do when responding to an email.
The one that is becoming a part of digital identity is responding to a mail. The correct option is D.
What is digital identity?A digital identity is the body of information that exists online about an individual, organization, or electronic device. Individuals or their devices can be identified using unique identifiers and usage patterns.
Your Digital Identity allows you to prove who you are online for work, education, and personal purposes, and you can use it again and again.
Before any of your details are shared with the service you want to access, you will be asked to give consent each time you use your Digital Identity.
Thus, the correct option is D.
For more details regarding digital identity, visit:
https://brainly.com/question/26077914
#SPJ1
What color object would reflect more light?
O Red
O Black
O Blue
o White
Answers
Answer:
White
Explanation:
Red absorbs all light except red light, which it reflects
Black absorbs all light
Blue absorbs all light except blue light, which it reflects
White reflects all light because it has all colors except black.
Hope you do well!
In step 5 of this activity, you created the number canceled column to represent the total number of canceled bookings. What value was returned in this column? 1 point 40234 44224 49550 52965
Answers
The value returned in the number canceled column was 44224. This number represents the total number of canceled bookings.
What is bookings?Bookings is a term used to refer to the process of reserving or booking a service, product, or facility. This can be done through a variety of different methods, including online, over the phone, or in person. Bookings are often used in the hospitality industry to reserve hotel rooms, restaurant tables, and tickets to events. Booking systems have become increasingly popular with the advent of the internet, as they allow customers to book services without having to wait in line, call a customer service representative, or visit a physical location. Bookings also provide customers with a convenient way to check availability, compare prices, and make payment for their purchase.
To learn more about bookings
https://brainly.com/question/29992362
#SPJ1
One way to check if a website is secure is to look for a/an
in the address bar.
Answers
Answer:
One such sign to look for is in the URL of the website. A secure website's URL should begin with “https” rather than “http”. The “s” at the end of “http” stands for secure and is using an SSL (Secure Sockets Layer) connection. Your information will be encrypted before being sent to a server.
T - True. One way to check if a website is secure is to look for a padlock icon in the address bar.
How does this work?This padlock indicates that the website is using a secure HTTPS connection. HTTPS encrypts the data transmitted between the user's browser and the website, ensuring that sensitive information such as login credentials or financial details remains private and protected from unauthorized access.
Additionally, a secure website's address will start with "https://" instead of "http://". Users should always verify these security indicators before entering any personal or sensitive information on a website to safeguard their online privacy and security.
Read more about websites here:
https://brainly.com/question/28431103
#SPJ2
when a coin object is passed to the println method
Answers
When a coin object is passed to the println method to obtain the string to print, the object's toString function is invoked.
Prints an object, followed by the line's end. The first String is called by this method. valueOf(x) retrieves the string value of the printed object and then acts as though print(String) and println() were being called. The console area, a black rectangle at the bottom of the Processing environment, is where the println() function writes. This feature is frequently useful for examining the data that a program generates. This function generates a new line of output with each call. The parameter to this function in String is a println() in Java, which is also used to display text on the console.
Learn more about println here:-
https://brainly.com/question/28719789
#SPJ4
a ____________ is a solid line of defense against malware and other security threats.
Answers
A firewall is a solid line of defense against malware and other security threats. A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
It acts as a barrier between a trusted internal network and untrusted external networks, such as the Internet. Here's how a firewall works:
1. Packet filtering: A firewall examines packets of data as they travel across the network. It analyzes the source and destination IP addresses, ports, and other packet information to determine whether to allow or block the traffic. For example, if a packet's source IP address matches a rule that permits outgoing web traffic, the firewall allows it to pass through. Otherwise, it may block the packet.
2. Stateful inspection: In addition to packet filtering, firewalls can also perform a stateful inspection. This means they keep track of the state of network connections. For example, if a computer inside the network initiates an outgoing connection to a website, the firewall can remember the connection and allow the corresponding incoming traffic from the website. This prevents unauthorized traffic from entering the network.
3. Application-level filtering: Some advanced firewalls can perform deep packet inspection, which means they can analyze the contents of network traffic at the application layer. This allows them to detect and block specific types of threats, such as malicious code embedded in web pages or email attachments.
4. Intrusion prevention: Firewalls can also incorporate intrusion prevention systems (IPS) to detect and block known patterns of malicious activity. An IPS analyzes network traffic in real-time and can identify and block potential threats, such as suspicious behavior or known attack signatures.
Overall, a firewall acts as a first line of defense against malware and other security threats by controlling and filtering network traffic. It helps protect the network and the devices connected to it from unauthorized access, data breaches, and other malicious activities.
Read more about Malware at https://brainly.com/question/29650348
#SPJ11